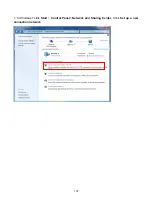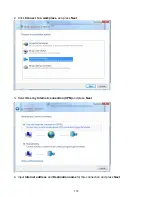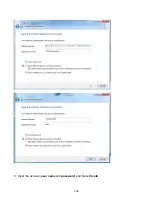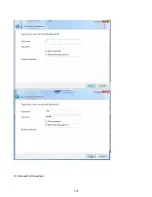
188
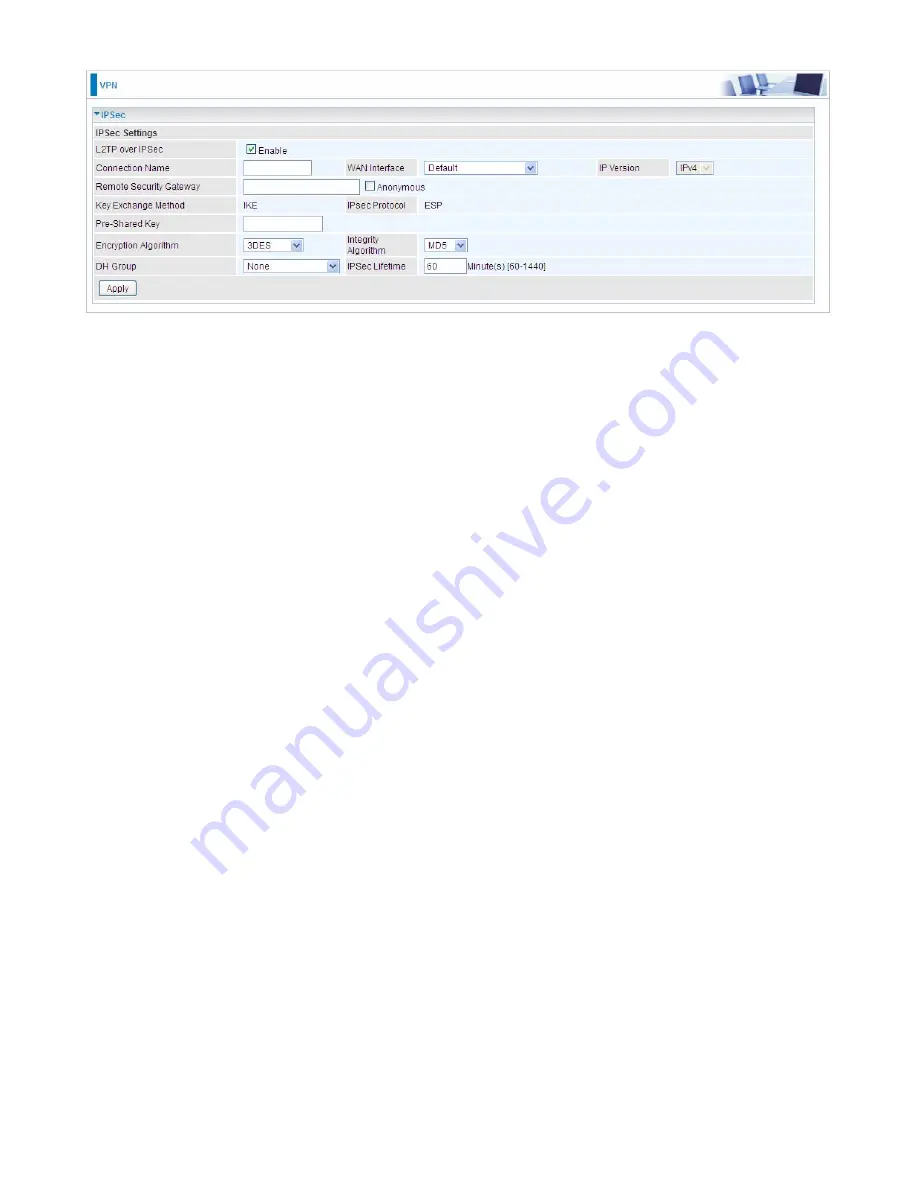
IPSec for L2TP
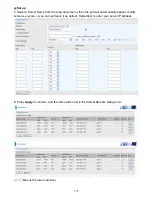
Connection Name:
A given name for the connection, but it should contain no spaces (e.g.
“connection-to-office”).
WAN Interface:
Select the set interface for the IPSec tunnel.
Remote Security Gateway:
Input the IP of remote security gateway.
Key Exchange Method:
Displays key exchange method.
Pre-Shared Key:
This is for the Internet Key Exchange (IKE) protocol, a string from 4 to 128
characters. Both sides should use the same key. IKE is used to establish a shared security policy
and authenticated keys for services (such as IPSec) that require a key. Before any IPSec traffic can
be passed, each router must be able to verify the identity of its peer. This can be done by manually
entering the pre-shared key into both sides (router or hosts).
Encryption Algorithm:
Select the encryption algorithm from the drop-down menu. There are
several options: 3DES and AES (128, 192 and 256). 3DES and AES are more powerful but
increase latency.
DES:
Stands for Triple Data Encryption Standard, it uses 56 bits as an encryption method.
3DES:
Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an encryption
method.
AES:
Stands for Advanced Encryption Standards, you can use 128, 192 or 256 bits as
encryption method.
Integrity Algorithm:
Authentication establishes the integrity of the datagram and ensures it is not
tampered with in transmit. There are 2 options: Message Digest 5 (MD5) and Secure Hash
Algorithm (SHA1). SHA1 is more resistant to brute-force attacks than MD5. However, it is slower.
MD5:
A one-way hashing algorithm that produces a 128
−
bit hash.
SHA1:
A one-way hashing algorithm that produces a 160
−
bit hash.
DH Group:
It is a public-key cryptography protocol that allows two parties to establish a shared
secret over an unsecured communication channel (i.e. over the Internet). MODP stands for Modular
Exponentiation Groups.
IPSec Lifetime:
Specify the number of minutes that IPSec will stay active before new encryption
and authentication key will be exchanged. Enter a value to negotiate and establish secure
authentication. Default is 60 minutes (3600 seconds). A short time increases security by forcing the
two parties to update the keys. However, every time when the VPN tunnel re- negotiates, access
through the tunnel will be temporarily disconnected.
Summary of Contents for 7800DX
Page 19: ...15 3G LTE Router mode ...
Page 37: ...33 Click link 192 168 1 254 it will lead you to the following page ...
Page 40: ...36 Click 192 168 1 254 it will lead you to the following page ...
Page 43: ...39 Click 192 168 1 254 it will lead you to the following page ...
Page 99: ...95 Configure AP as Enrollee Add Registrar with PIN Method 1 Set AP to Unconfigured Mode ...
Page 143: ...139 Accessing mechanism of Storage In your computer Click Start Run enter 192 168 1 254 ...
Page 145: ...141 Access the folder public ...
Page 148: ...144 Step 2 Click Add a Printer Step 3 Click Add a network wireless or Bluetooth printer ...
Page 159: ...155 Rule inactive ...
Page 186: ...182 ALG The ALG Controls enable or disable protocols over application layer ...
Page 194: ...190 ...
Page 197: ...193 ...
Page 204: ...200 5 Input the account user name and password and press Create ...
Page 205: ...201 6 Connect to the server ...
Page 206: ...202 7 Successfully connected ...
Page 208: ...204 ...
Page 219: ...215 4 Input Internet address and Destination name for this connection and press Next ...
Page 220: ...216 5 Input the account user name and password and press Create ...
Page 238: ...234 2 ipoe_eth0 with DDNS www hometest1 com using username password test test ...
Page 251: ...247 Click Apply to confirm your settings ...
Page 262: ...258 Example Ping www google com ...
Page 263: ...259 Example trace www google com ...