3.
At the Port Number selection, enter a source port that is not being used by another NIM
on the same network (such as 7701, 7702, 7703, and so on). Keeping a list of the
network modules on a particular network along with the source ports of those modules
will ensure that duplicate source ports are not used.
4.
At the Datagram selection, enter 07 and press Enter.
5.
At the Remote Port selection, enter the port number that is used in the D6680/D6682 for
the D6600.
6.
Save the settings and exit from the setup of the NIM.
Outgoing packets from a network over a single IP address go through a router or firewall that
uses NAT tables to keep track of which packets come from which internal IP addresses. The
NAT table ensures that the returning packets for a device are forwarded to the device that
sent out the first packet. An example of this is multiple PCs on a network connecting to the
Internet through a single IP address from an ISP. By using the same idea, network devices can
perform the same function.
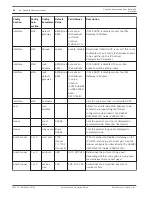
The following table shows an example of what the NAT table remembers when packets are
sent to a destination. An outgoing packet is sent to an IP address with Source and Destination
ports in that packet. The Destination port is the port number that the device uses when it
receives data. After receiving the data, the device processes it and sends a packet back to the
IP address that sent the data.
Internal IP Address
Source Port
192.168.1.11
7700
192.168.1.12
7701
192.168.1.13
7702
When the data is returned to the router or firewall software, the NIM directs the returning
packet to the correct internal IP address based on the NAT table.
Networking and Encryption
i
Notice!
If you are considering using or are currently using networking and encryption, read the follow-
ing information carefully.
In all cases, encryption is performed in the NIM (Network Interface Module) that is used in the
D6686/D6682/D6680, D9133TTL-E, C900V2/C900TTL-E, and DX4020. When using a B420 or
B426 on a GV4 v1.x control panel, encryption is performed in the NIM. Starting with GV4 v2.0
and the B Series control panels, encryption is done in the control panel. When encryption is
used, the encryption key coming to the D6600 must be the same key used on all field devices
that are reporting to that IP address. Because you can use up to two NIMs on the D6600,
several combinations can be used:
–
Both NIMs using encryption – two NIMs can use different keys or the same key
–
One NIM using encryption, the other not using encryption
–
Neither NIM using encryption
If encryption is On in the NIM at the D6600, then it must be On in the field devices. If it is Off
in the NIM at the D6600, then it must be Off in the field devices.
–
If you are not currently using encryption, refer to Using Encryption for the First Time, page
55.
–
If you are currently using encryption, refer to Upgrading Encryption, page 55.
12.2.4
54
en | Network Communications
Conettix Communications Receiver/
Gateway
2012.11 | 08 | 4998122704
Installation and Operation Guide
Bosch Security Systems, Inc.
Summary of Contents for Conettix D6100IPv6
Page 1: ...Conettix Communications Receiver Gate way D6600 D6100IPv6 en Installation and Operation Guide ...
Page 2: ......
Page 86: ......
Page 87: ......