Central Site Remote Access Switch 307
C
ONFIGURING
A
DVANCED
IP R
OUTING
IP Filters
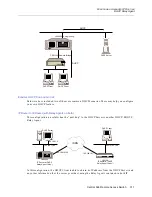
The corporate dial-in access is realized with a WAN Direct Interface, using a pool of IP addresses
from the corporate LAN for dynamic assignment to the dial-in devices. These devices must first
pass Authentication processing, so there is a level of security inherent on this interface that is not
present on the Internet interface. Once authenticated, the devices are basically allowed to generate
traffic in the same way that they can when operating from within the corporate LAN. This includes
the ability to initiate TCP connections to the external Internet. Correspondingly, the strategy for this
filter is different. Its purpose is to enforce the stated requirement of not allowing any external access
to the Netserver or the CyberSWITCH itself.
Now suppose that a situation arises in which it is temporarily necessary to allow remote access to
the Netserver (for example, reconfiguration by a qualified member of staff who is offsite). Using the
IP Address from which the temporary access will take place, this can be accomplished by enabling
the Exception Filter. When traffic arrives from the Internet, the Exception filter will be executed
first, thereby allowing an override of the existing conditions of the Input filter. The Exception filter
would be set up as follows (the remote access is originated from address 201.55.89.100).
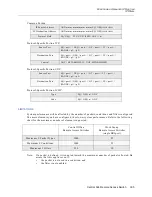
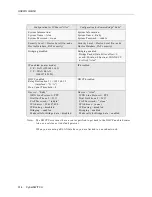
FORWARD
IP Src 0.0.0.0, 0.0.0.0
IP Dst: 255.255.255.255, 128.131.25.10
IP Prot: ANY
Permits any host to access the FTP
Server.
FORWARD
IP Src 0.0.0.0, 0.0.0.0
IP Dst: 255.255.255.255, 128.131.25.12
IP Prot: ANY
Permits any host to access the WWW
Server
FORWARD
IP Src 0.0.0.0, 0.0.0.0
IP Dst: 0.0.0.0., 0.0.0.0
IP Prot: TCP
TCP Src Port: RANGE 0 65535
TCP Dst Port: RANGE 0 65535
TCP Control: ESTABLISHED
Permits TCP traffic only from sessions
which have already been initiated by
corporate hosts.
FORWARD
IP Src 0.0.0.0, 0.0.0.0
IP Dst: 0.0.0.0., 0.0.0.0
IP Prot: ICMP
Permits all ICMP packets to enter (in-
cluding ECHO packets for PING).
DISCARD
All other packet types
No-match action.
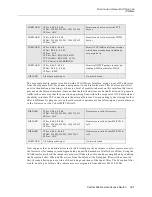
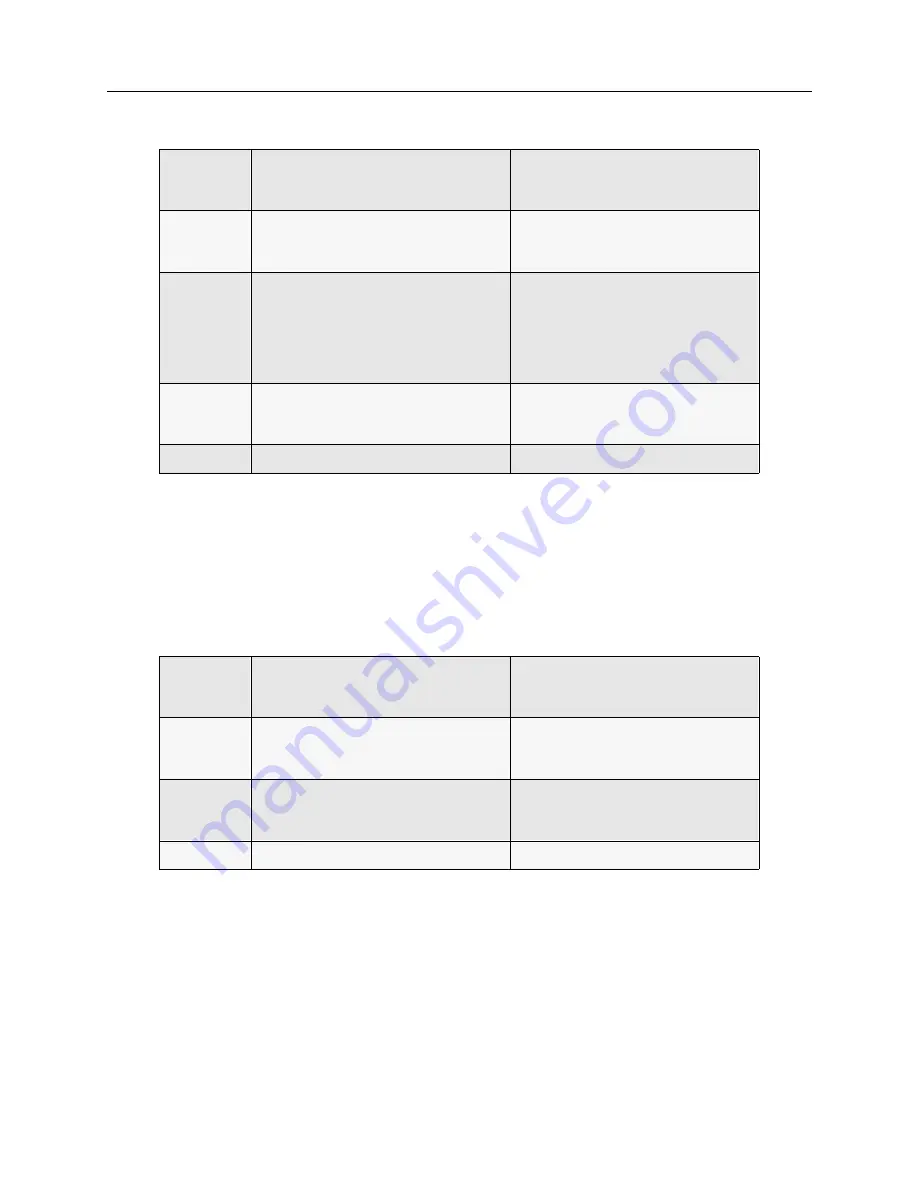
DISCARD
IP Src 0.0.0.0, 0.0.0.0
IP Dst: 255.255.255.255, 128.131.25.11
IP Prot: ANY
Denies access to the Netserver.
DISCARD
IP Src 0.0.0.0, 0.0.0.0
IP Dst: 255.255.255.255, 128.131.25.15
IP Prot: ANY
Denies access to the CyberSWITCH it-
self.
DISCARD
IP Src 0.0.0.0, 0.0.0.0
IP Dst: 255.255.255.255, 193.57.50.1
IP Prot: ANY
Denies access to the CyberSWITCH it-
self.
FORWARD
All other packet types
No-match action