Chapter 1: Configuration
Configuring a RADIUS server
Page
1-301
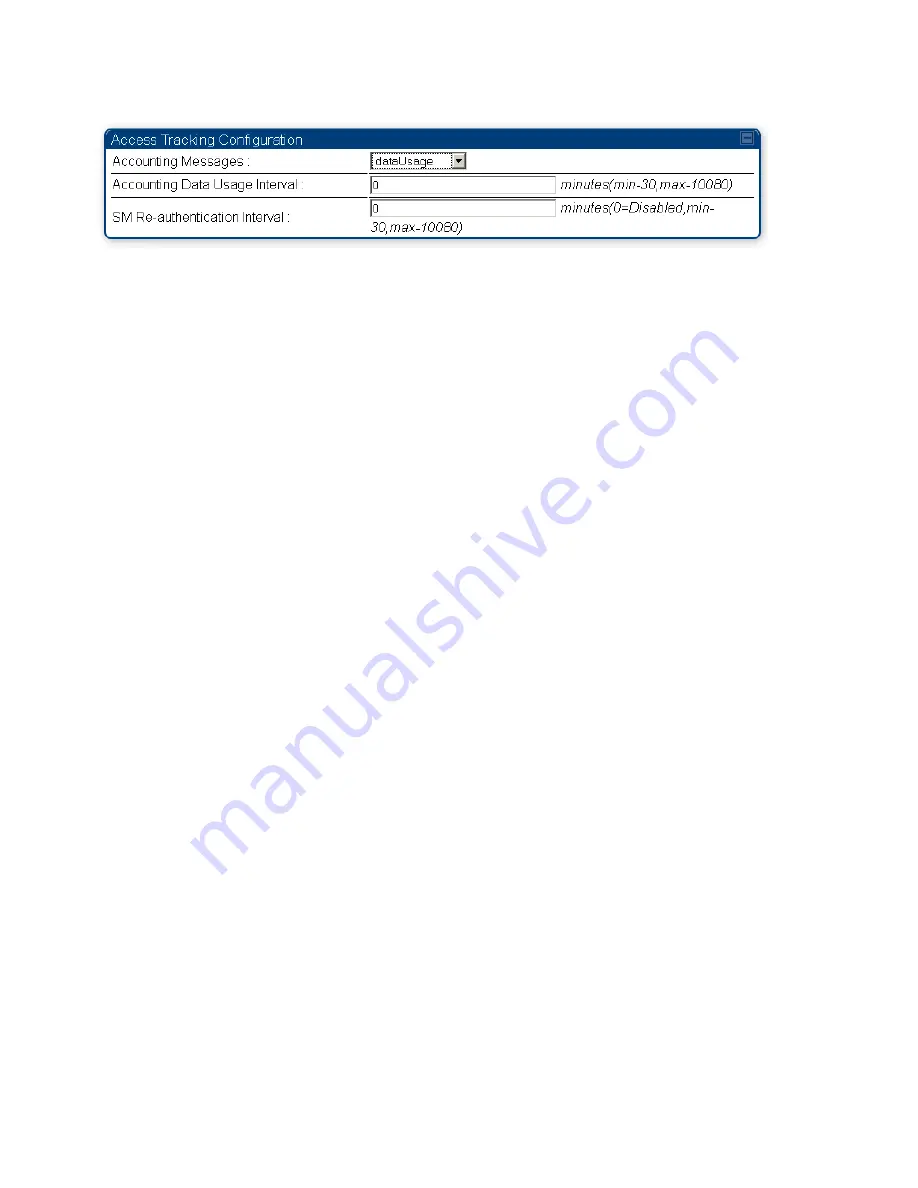
Figure 51 Device re-authentication configuration
The re-authentication interval is only configurable on the AP. When this feature is enabled, each SM that
enters the network will re-authenticate each the interval time has expired without dropping the session.
The response that the SM receives from the AAA server upon re-authentication is one of the following:
•
Success: The SM continues normal operation
•
Reject: The SM de-registers and will attempt network entry again after 1 minute and then if rejected
will attempt re-entry every 15 minutes
•
Timeout or other error: The SM remains in session and attempt 5 times to re-authenticate with the
RADIUS-REQUEST message. If these attempts fail, then the SM will go out of session and proceed to
re-authenticate after 5 minutes, then every 15 minutes.
Although re-authentication is an independent feature, it was designed to work alongside with the
RADIUS data usage accounting messages. If a user is over their data usage limit the network operator
can reject the user from staying in the network. Operators may configure the RADIUS ‘Reply-Message’
attribute with an applicable message (i.e. “Data Usage Limit Reached”) that is sent to the subscriber
module and displayed on the general page.
Summary of Contents for PMP 450 AP
Page 51: ...Chapter 1 Configuration Quick link setup Page 1 23 ...
Page 155: ...Chapter 1 Configuration Configuring security Page 1 127 ...
Page 163: ...Chapter 1 Configuration Configuring security Page 1 135 ...
Page 164: ...Chapter 1 Configuration Configuring security Page 1 136 ...
Page 193: ...Chapter 1 Configuration Configuring radio parameters Page 1 165 ...
Page 194: ...Chapter 1 Configuration Configuring radio parameters Page 1 166 ...
Page 195: ...Chapter 1 Configuration Configuring radio parameters Page 1 167 ...
Page 206: ...Chapter 1 Configuration Configuring radio parameters Page 1 178 ...
Page 210: ...Chapter 1 Configuration Configuring radio parameters Page 1 182 ...
Page 636: ...Chapter 5 Troubleshooting Logs Page 5 16 Figure 95 SM Authorization log ...
















































