Release Notes
System Release 13.4
pmp-0979 - July 2015
Page
10 of
50
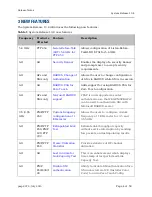
3.3
RADIUS Change of Authorization
Prior to 13.4 release, SM will get configuration parameters from a RADIUS server during
authentication process. This feature allows an administrator to control configuration
parameters in the SM while SM is in session. The configuration changes in SM are done
using RADIUS Change of Authorization method (RFC 3576) on the existing RADIUS
authentication framework for AP and SM. A typical use case could be changing the QOS
parameters after a certain amount of bandwidth usage by a SM.
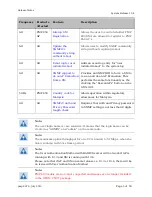
The RADIUS CoA feature enables initiating a bi-directional communication from the
RADIUS server(s) to the AP and SM.
The AP listens on UDP port 3799 and accepts CoA requests from the configured RADIUS
servers. This CoA request should contain SM MAC address in ‘User-Name’ attribute as
identifier and all other attributes which control the SM config parameters. For security
reasons, a timestamp also needs to be added as ‘Event-Timestamp’ attribute. Hence the
time should also be synchronized between the RADIUS server(s) and the AP to fit within a
window of 300 seconds.
Once the configuration changes are applied on the SM, CoA-ACK message is sent back to
RADIUS server. If the validation fails, the AP sends a CoA-NACK response to the RADIUS
server with proper error code.
Note:
The RADIUS CoA feature will only enabled if Authentication mode is set to
RADIUS AAA
.
Web Management Interface
The CoA Feature can be enabled or disabled under
Configuration > Security >
Authentication
Server Settings
tab.
The feature is disabled by default.