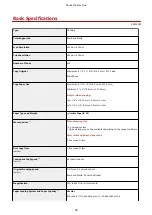
Certificate signature algorithm
RSA: SHA-256, SHA-384
*3
, SHA-512
*3
ECDSA: SHA-256, SHA-384, SHA-512
*1
Requirements for the certificate contained in a key are pursuant to CA certificates.
*2
Certificates of more than 2 MB cannot be registered.
*3
SHA384-RSA and SHA512-RSA are available only when the RSA key length is 1024 bits or more.
●
The machine does not support use of a certificate revocation list (CRL).
Definition of "Weak Encryption"
When [Prohibit Use of Weak Encryption] in [Encryption Settings] is set to [On], the use of the following algorithms is
prohibited. [Encryption Settings](P. 514)
Hash
MD4, MD5, SHA-1
HMAC
HMAC-MD5
Common key encryption
RC2, RC4, DES
Public key encryption
RSA encryption (512 bits/1024 bits)
RSA signature (512 bits/1024 bits)
DSA (512 bits/1024 bits)
DH (512 bits/1024 bits)
●
Even when [Prohibit Key/Cert. with Weak Encryption] in [Encryption Settings] is set to [On], the hash
algorithm SHA-1, which is used for signing a root certificate, can be used.
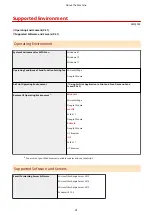
TLS
The following combinations of the TLS version and algorithm are usable:
: Usable
: Not usable
Algorithm
TLS Version
TLS 1.3 TLS 1.2 TLS 1.1 TLS 1.0
Encryption Algorithm
About the Machine
39
Summary of Contents for imageCLASS MF264dw
Page 72: ... Shared Key Encryption for WPA WPA2 TKIP AES CCMP IEEE 802 1X Authentication Setting Up 63 ...
Page 139: ...Basic Operations 130 ...
Page 204: ... The volume is adjusted Basic Operations 195 ...
Page 333: ...Copying 324 ...
Page 368: ...8 Log out from Remote UI Security 359 ...
Page 501: ... Confirm Destination Scan PC Settings Menu Items 492 ...