Concerning the Information Security Standard
4XR3-0H5
This machine is compliant with IEEE Std. 2600™-2008 (IEEE 2600), an international standard concerning information
security for multifunctional peripherals and printers. This section describes the security requirements defined in IEEE
2600, and the corresponding machine functions.
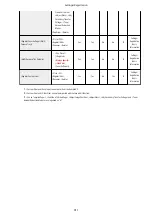
Security requirement
Corresponding machine function
Preventing unauthorized access with user
authentication/user information management
User Authentication
Performs personal authentication based on user authentication information
such as user names and passwords, and manages user information such as
privileges (roles). Managing Users(P. 675)
Managing access and restricting operations by user
ACCESS MANAGEMENT SYSTEM
The availability of functions such as printing and copying can be assigned to
each user, enabling you to manage access to these functions on an
individual user basis. See ACCESS MANAGEMENT SYSTEM Administrator
Guide.
Using audit logs
*1
to record and monitor security-
related user operations
Generating/exporting audit logs
You can record user authentication logs and job logs, and export them from
the Remote UI. Managing the Logs(P. 822)
Completely deleting unnecessary data from the hard
disk
HDD Complete Deletion
Unnecessary data can be deleted from the hard disk by overwriting with
random data multiple times. Managing Hard Disk Data(P. 890)
Protecting the various types of data and confidential
information stored on the hard disk
*2
Hard disk data encryption
Encryption is used to protect data on the hard disk, such as files stored in
the Mail Box, Address Book data, and password information. Managing
Hard Disk Data(P. 890)
Protecting data on the network with encrypted
communication
IPSec
By creating security policies for encrypted communication, data can be
protected from various threats when sent and received over an IP network.
Configuring the IPSec Settings(P. 743)
Self-verification of security functions
IPSec
When IPSec is enabled, the self-test for the encryption module is
automatically performed when the machine starts.
*1 Operations for <Scan and Store>, <Network> in <Access Stored Files>, and <Memory Media> are not included in the scope of the audit.
*2 Files stored in memory media are not encrypted.
Managing the Machine
899
Summary of Contents for imageRUNNER ADVANCE C5535i III
Page 16: ...Setting Advanced Box to Public 79 Connecting to the Other Devices 84 Setting Up 2 ...
Page 37: ...LINKS Adapting to the Network Environment P 43 Setting Up 23 ...
Page 65: ...4 Press OK 5 Press Yes Setting Up 51 ...
Page 87: ...LINKS Faxing P 384 Options P 1513 Setting Up 73 ...
Page 119: ...Basic Operations 105 ...
Page 176: ...Starting the Remote UI P 784 Basic Operations 162 ...
Page 184: ...LINKS Hardware Specifications P 1485 Basic Operations 170 ...
Page 222: ... If you do not want to register settings select Unassigned Basic Operations 208 ...
Page 229: ...4 Press OK Basic Operations 215 ...
Page 279: ...7 Press Copying starts Copying 265 ...
Page 294: ...8 Press Start Copying Copying starts Copying 280 ...
Page 298: ... Copying starts Copying 284 ...
Page 322: ...8 Press Copying starts LINKS Making Booklets Booklet Copying P 299 Copying 308 ...
Page 337: ... Copying starts LINKS Inserting Sheets and Chapter Pages Insert Sheets P 317 Copying 323 ...
Page 344: ... Maximum number of job blocks that can be scanned 100 Copying 330 ...
Page 359: ...7 Select the number of sheets and press OK 8 Press Copying starts Copying 345 ...
Page 461: ...3 Click General Settings 4 Click Add Destination Faxing 447 ...
Page 513: ...LINKS Registering Destinations P 218 Scanning 499 ...
Page 543: ...Erasing Dark Borders When Scanning Erase Frame P 523 Scanning 529 ...
Page 549: ...Specifying E Mail Settings P 559 Scanning 535 ...
Page 641: ... N on 1 Print Comments Password to Open Doc Skip Blank Pages Using Storage Space 627 ...
Page 665: ...6 Click Fax Fax sending starts Linking with Mobile Devices 651 ...
Page 747: ...LINKS Specifying IP Addresses in Firewall Settings P 729 Managing the Machine 733 ...
Page 752: ...4 Press Apply Set Changes Yes Managing the Machine 738 ...
Page 782: ...LINKS Configuring the Forced Hold Printing Settings P 761 Managing the Machine 768 ...
Page 787: ...Restricting Copying Using a QR Code P 355 Managing the Machine 773 ...
Page 801: ...Settings Registration P 905 Managing the Machine 787 ...
Page 806: ...Starting the Remote UI P 784 Managing the Machine 792 ...
Page 1124: ... The reception speed set in RX Start Speed RX Start Speed P 1117 Settings Registration 1110 ...
Page 1237: ...6 Press OK Maintenance 1223 ...
Page 1453: ...Managing MEAP Applications P 1443 Managing MEAP Application Licenses P 1448 Appendix 1439 ...
Page 1507: ...Appendix 1493 ...
Page 1580: ...5 Close the right cover of the machine Appendix 1566 ...
Page 1595: ... 5 iproute 284 Squid 295 gst plugins base 341 webkit 352 ...
Page 1650: ... 60 libjpeg this software is based in part on the work of the Independent JPEG Group ...
Page 1663: ... 73 MD4 RSA Data Security Inc MD4 Message Digest Algorithm ...
Page 1850: ... 260 This file is distributed without any expressed or implied warranty ...
Page 2019: ...introduced by others ...