IPS-1
pure
security
™
pure
security
™
anomaly detection, protocol analysis, operating system and
application fingerprinting, smart IP reassembly, multi-element
correlation, and dynamic worm mitigation. This robust detec-
tion engine enables broad coverage across the threat
spectrum, ensuring IT assets are protected against known
and unknown threats.
attack confidence indexing
IPS-1 includes a unique feature called Attack Confidence
Indexing that enables administrators to direct and calibrate
prevention enforcement according to factors such as the
threat and asset under attack. Attack Confidence Indexing
allows known exploits to be blocked with no concern of
blocking critical business traffic.
Multi-alert correlation
Multi-alert Correlation identifies patterns in alert activity that
would otherwise be reported as separate, unrelated events.
For example, a single source IP launching multiple attacks
across a geographically distributed network would be
correlated and raised as a higher priority correlated alert.
Dynamic worm Mitigation
Dynamic Worm Mitigation recognizes rapidly propagating
worms and automatically blocks them from proliferating
across your entire network.
aware, adaptive, and actionable security
IPS-1 automatically recognizes threat points and dynamically
protects them against inevitable attack. IPS-1 determines
critical vulnerabilities and changes in the network, alerts
security managers to these threatened points, and automati-
cally deploys the proper signature sets to protect them before
they are attacked.
ongoing security updates via SmartDefense Services
IPS-1 systems are backed by Check Point SmartDefense
™
Services, which provide ongoing, real-time updates and
security advisories, helping ensure that Check Point
security solutions are continuously updated to stay ahead of
today’s constantly evolving threats. Security experts at the
SmartDefense Research Center continuously monitor the
Internet for new exploits and vulnerabilities and rapidly
develop and deliver new protections to help ensure that your
network and business are protected from evolving threats.
the ManaGeMent to SolVe Data oVerloaD
Only IPS-1 delivers the management tools required to keep
your administrators from drowning in data and starving for
critical, actionable information.
Situational Visibility
IPS-1 provides instant awareness of only what’s important—
important security events associated with business-critical
systems. A real-time graphical interface isolates and high-
lights critical attacks against essential business systems
accelerating the ability to recognize, evaluate, and act upon
truly critical events. This “at a glance” monitoring not only
makes operators of any skill level more efficient, but a simple
mouse click allows them to quickly and easily evaluate critical
events, set response, and remediation actions.
advanced forensic analysis
IPS-1 allows you to quickly sort through an overload of alert
information to identify actionable events and their patterns,
including the attack source, attack methods, severity, targets,
frequency, and many others. From there, a single mouse click
provides alert detail information including attack description,
effect, importance, remediation, third-party information
sources, and more.
packet capture
View deep forensic analysis and packet capture information
of attacks.
alert flood suppression
Alert flood suppression recognizes and automatically consoli-
dates bursts of alert floods and presents them as a single
consolidated alert rather than an unmanageable flood of
alerts on your screen.
top 10 graphs
Delivers quick and exacting graphical views of the “Top 10”
attackers, attack targets, protocols, and so on.
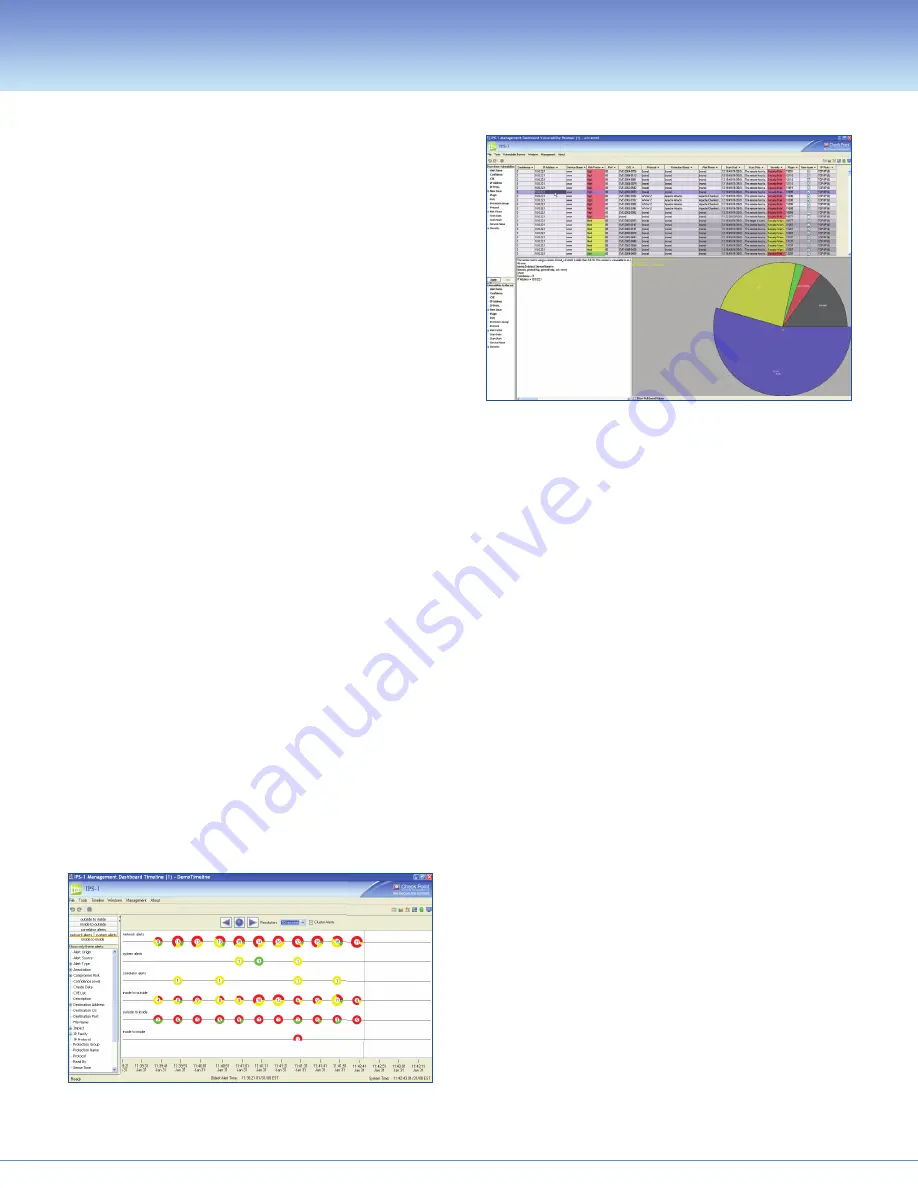
An intuitive Timeline View makes it easy for administrators to analyze
alerts that appeared within a particular time period.
The IPS-1 Vulnerability Browser enables vulnerability scanning,
viewing, and management from a single dashboard.














