4-48
Cisco Wireless LAN Controller Configuration Guide
OL-17037-01
Chapter 4 Configuring Controller SettingsWireless Device Access
Configuring Quality of Service
Step 9
To define the maximum value (0–7) for the priority tag associated with packets that fall within the
profile, enter these commands:
config qos protocol-type
{bronze | silver | gold | platinum} dot1p
config qos dot1p-tag
{bronze | silver | gold | platinum}
tag
Step 10
To re-enable the 802.11a and 802.11b/g networks so that you can configure the QoS profiles, enter these
commands:
config 802.11a enable network
config 802.11b enable network
Step 11
Follow the instructions in the
“Assigning a QoS Profile to a WLAN” section on page 6-30
to assign a
QoS profile to a WLAN.
Configuring Quality of Service Roles
After you configure a QoS profile and apply it to a WLAN, it limits the bandwidth level of clients
associated to that WLAN. Multiple WLANs can be mapped to the same QoS profile, which can result in
bandwidth contention between regular users (such as employees) and guest users. In order to prevent
guest users from using the same level of bandwidth as regular users, you can create QoS roles with
different (and presumably lower) bandwidth contracts and assign them to guest users.
You can use the controller GUI or CLI to configure up to ten QoS roles for guest users.
Note
If you choose to create an entry on the RADIUS server for a guest user and enable RADIUS
authentication for the WLAN on which web authentication is performed rather than adding a guest user
to the local user database from the controller, you need to assign the QoS role on the RADIUS server
itself. To do so, a “guest-role” Airespace attribute needs to be added on the RADIUS server with a
datatype of “string” and a return value of “11.” This attribute is sent to the controller when authentication
occurs. If a role with the name returned from the RADIUS server is found configured on the controller,
the bandwidth associated to that role is enforced for the guest user after authentication completes
successfully.
Using the GUI to Configure QoS Roles
Follow these steps to configure QoS roles using the controller GUI.
Step 1
Click
Wireless
>
QoS > Roles
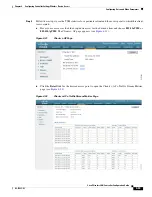
to open the QoS Roles for Guest Users page (see