© Copyright 2007 Cisco Systems, Inc.
This document may be freely reproduced and distributed whole and intact including this Copyright Notice.
19
The tamper evidence seals are produced from a special thin gauge vinyl with self-adhesive
backing. Any attempt to open the router will damage the tamper evidence seals or the material of
the module cover. Since the tamper evidence seals have non-repeated serial numbers, they can be
inspected for damage and compared against the applied serial numbers to verify that the module
has not been tampered. Tamper evidence seals can also be inspected for signs of tampering,
which include the following: curled corners, bubbling, crinkling, rips, tears, and slices. The word
“OPEN” may appear if the label was peeled back.
2.5 Cryptographic Key Management
The router securely administers both cryptographic keys and other critical security parameters
such as passwords. The tamper evidence seals provide physical protection for all keys. All keys
are also protected by the password-protection on the Crypto Officer role login, and can be
zeroized by the Crypto Officer. All zeroization consists of overwriting the memory that stored
the key. Keys are exchanged and entered electronically or via Internet Key Exchange (IKE) or
SSL handshake protocols.
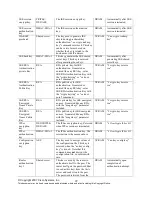
The routers support the following FIPS-2 approved algorithm implementations:
Algorithm
Algorithm Certificate Number
Software (IOS) Implementations
AES
795
Triple-DES
683
SHA-1, SHA-256, SHA-512
794
HMAC-SHA-1
436
X9.31 PRNG
456
RSA
379
Onboard NetGX Implementations
AES
265
Triple-DES
347
SHA-1
344
HMAC-SHA-1
77
AIM Module Implementations
AES
100
Triple-DES
213
SHA-1
401
HMAC-SHA-1
38
X9.31 PRNG
80
RSA
383
The router is in the approved mode of operation only when FIPS 140-2 approved algorithms are
used (except DH and RSA key transport which are allowed in the approved mode for key
establishment despite being non-approved).
Note: The module supports DH key sizes of 1024 and 1536 bits and RSA key sizes of 1024,
1536 and 2048 bits. Therefore, the Diffie Hellmann Key agreement, key establishment
methodology provides between 80-bits and 96-bits of encryption strength per NIST 800-57. RSA