Cisco Cat4K NDPP ST
11 March 2014
EDCS-1228241
65
TOE SFRs
How the SFR is Met
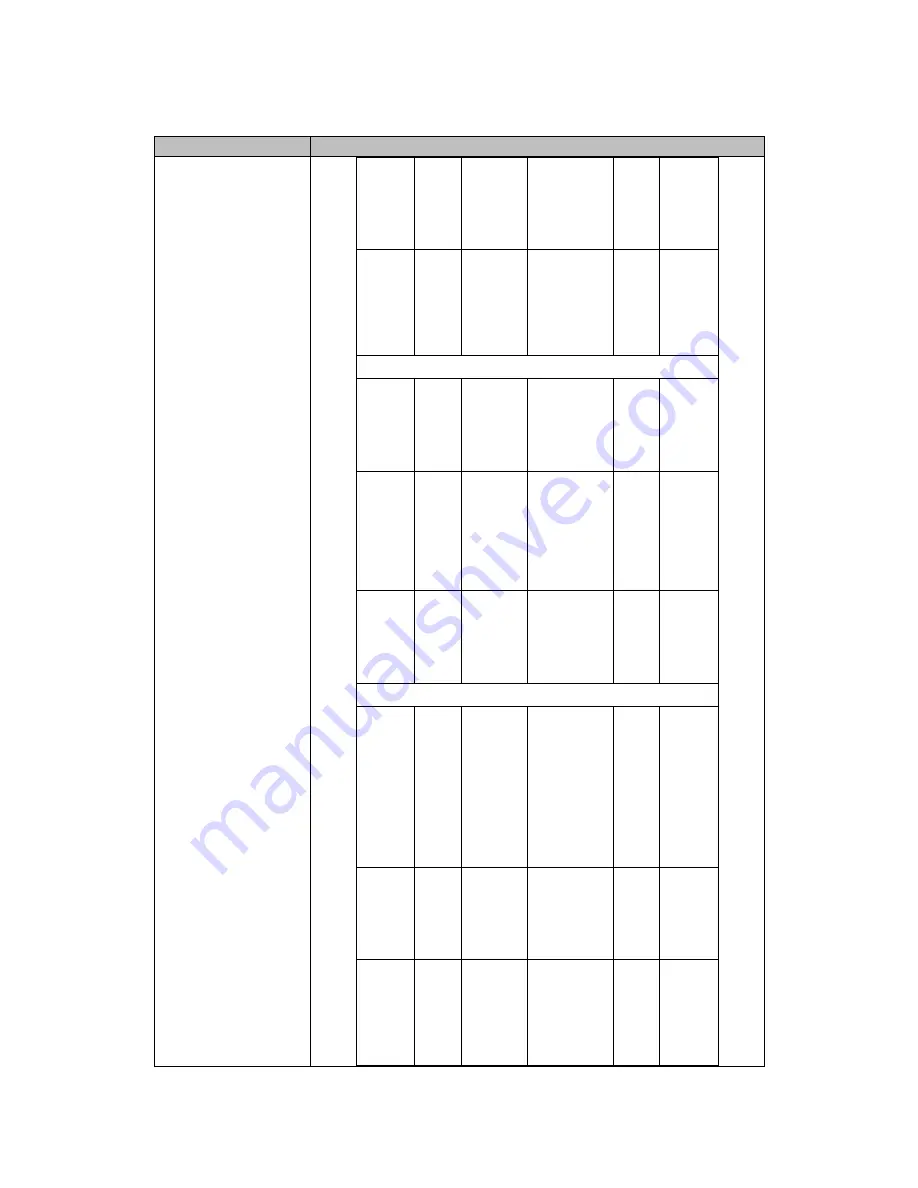
d.
Overwritt
en with:
0x00
SSH
session
authentica
tion key
HMAC
SHA-1
160-bits
This is the SSH
session
authentication
key
DRAM
(plainte
xt)
Automati
cally
when
SSH
session
terminate
d
TLS
TLS
Server
RSA
private
key
RSA
1024/1536/
2048
bits
modulus
Identity
certificates for
module
itself
and also used
in
TLS
negotiations.
NVRA
M
(plainte
xt)
# fips
zeroize all
TLS pre-
master
secret
Shared
Secret
384-bits
Shared
secret
created
using
asymmetric
cryptography
from
which
new
HTTPS
session
keys
can be created.
DRAM
(plainte
xt)
Automati
cally
when
session
terminate
d.
TLS
session
key
Triple-
DES/A
ES
168-
bits/256-
bits
This is the TLS
session key
DRAM
(plainte
xt)
Automati
cally
when
session
terminate
d.
MacSec
MACsec
Security
Associati
on
Key
(SAK)
AES-
GCM
128/256
bits
Used
for
creating
Security
Associations
(SA)
for
encrypting/decr
ypting
the
MACSec
traffic in the
MACSec
hardware.
MACse
c PHY
(plainte
xt)
Automati
cally
when
session
expires
MACsec
Connectiv
ity
Associati
on
Key
(CAK)
AES-
GCM
128/256
bits
A secret key
possessed
by
members of a
MACSec
connectivity
association.
MACse
c PHY
(plainte
xt)
Automati
cally
when
session
expires
MACsec
KEK
AES-
GCM
128/256
bits
Used
to
transmit SAKs
to
other
members of a
MACSec
connectivity
association
MACse
c PHY
(plainte
xt)
Automati
cally
when
session
expires
















































