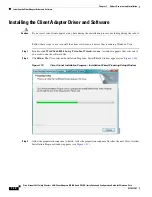
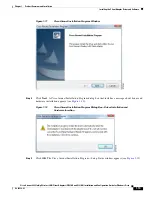
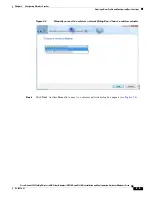
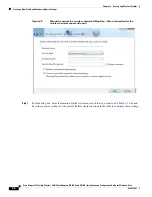
2-10
Cisco Aironet 802.11a/b/g Wireless LAN Client Adapters (CB21AG and PI21AG) Installation and Configuration Guide for Windows Vista
OL-16534-01
Chapter 2 Configuring Wireless Profiles
Security and Encryption Types
Security and Encryption Types
The dialog box in
Figure 2-5
includes the settings that allow you to configure how the client adapter
associates to an access point, authenticates to a wireless network, and encrypts and decrypts data. The
following sections provide explanations of options that are available in the Security type drop-down list,
the Encryption type drop-down list, and the Security Key/Passphrase field of this dialog box.
WEP (Shared) Security with Static WEP Keys
You can protect your data as it is transmitted through your wireless network by encrypting it through the
use of wired equivalent privacy (WEP) encryption keys. With WEP encryption, the transmitting device
encrypts each packet with a WEP key, and the receiving device uses that same key to decrypt each
packet.
The WEP keys used to encrypt and decrypt transmitted data can be statically associated with your client
adapter. Static WEP keys are either 40 or 128 bits in length. 128-bit WEP keys offer more security than
40-bit WEP keys.
Each profile can be assigned a static WEP keys. If the device receives a packet that is not encrypted with
the appropriate key (as the WEP keys of all devices that are to communicate with each other must match),
the device discards the packet and never delivers it to the intended receiver.
You do not need to re-enter the static WEP key each time the client adapter is inserted or the Windows
device is rebooted because the key is stored (in an encrypted format for security reasons) in the Windows
profile store.
You can obtain a static WEP key from your network administrator.
Note
WEP encryption is not considered safe enough for today’s wireless networks. We do not recommend that
you use it in enterprise wireless networks.
WPA and WPA2
Wi-Fi Protected Access (WPA) and WPA2
are standards-based security solutions from the Wi-Fi
Alliance that provide data protection and access control for wireless LAN systems. WPA is compatible
with the IEEE 802.11i standard but was implemented prior to the standard’s ratification; WPA2 is the
Wi-Fi Alliance’s implementation of the ratified IEEE 802.11i standard.
WPA and WPA2 can use Temporal Key Integrity Protocol (TKIP) and message integrity check (MIC)
for data protection or the stronger Advanced Encryption Standard encryption algorithm using Counter
Mode with Cipher Block Chaining Message Authentication Code Protocol (AES-CCMP). Both WPA
and WPA2 use 802.1X for authenticated key management.
Both WPA and WPA2 support two mutually exclusive key management types: WPA/WPA2 and
WPA/WPA2 passphrase (also known as WPA pre-shared key or WPA-PSK). Using WPA or WPA2,
clients and the authentication server authenticate to each other using an EAP authentication method, and
the client and server generate a pairwise master key (PMK). The server generates the PMK dynamically
and passes it to the access point. Using WPA or WPA2 passphrase, however, you configure a passphrase
(or pre-shared key) on both the client and the access point, and that passphrase is used as the PMK.