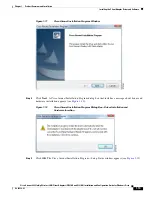
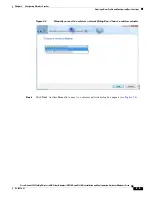
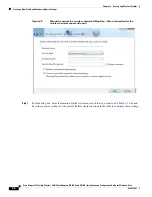
2-11
Cisco Aironet 802.11a/b/g Wireless LAN Client Adapters (CB21AG and PI21AG) Installation and Configuration Guide for Windows Vista
OL-16534-01
Chapter 2 Configuring Wireless Profiles
Security and Encryption Types
•
WPA2-Personal—WPA2 authentication with a preshared key. WPA2-Personal is suitable for
environments without a Remote Authentication Dial-In User Service (RADIUS) infrastructure (for
example, a small office or home office network). WPA2-Personal supports the use of a preshared
key (PSK).Obtain the preshared key from your system administrator. When you choose
WPA2-Personal as your security type, your encryption type is TKIP or AES.
•
WPA-Personal—WPA with a preshared key. Like WPA2-Personal, WPA-Personal is suitable for
environments without a RADIUS infrastructure. Obtain the preshared key from your system
administrator. When you choose WPA-Personal as your security type, your encryption type is TKIP
or AES.
•
WPA2-Enterprise—WPA2-Enterprise requires authentication in two phases: the first is an open
system authentication, and the second uses 802.1X with an Extensible Authentication Protocol
(EAP) authentication method. See chapter
Chapter 3, “Configuring EAP Types,”
for more
information about supported EAP methods. When you choose WPA2-Enterprise as your security
type, your encryption type is TKIP or AES.
•
WPA-Enterprise—WPA-Enterprise also uses 802.1X authentication and is designed for medium and
large infrastructure mode networks. See chapter for more information about supported EAP
methods. When you choose WPA-Enterprise as you security type, your encryption type is TKIP or
AES.
802.1X with Dynamic WEP Keys
The standard for wireless LAN security, as defined by IEEE, is called 802.1X for 802.11, or simply
802.1X. An access point that supports 802.1X and its protocol, Extensible Authentication Protocol
(EAP), acts as the interface between a wireless client and an authentication server, such as a RADIUS
server, to which the access point communicates over the wired network.
Dynamic WEP keys are created as part of the EAP authentication process. Dynamic WEP keys with EAP
offer a higher degree of security than static WEP keys.
When you choose the 802.1X with WEP encryption, you can configure the profile to use five different
authentication methods of dynamic WEP key creation:
•
Smart Card or other certificate—for more information about smart cards and other certification
authentication, go to the Microsoft site:
http://technet2.microsoft.com/windowsserver/en/library/7c6b414a-80c7-4bc1-b952-6eca6585dff9
1033.mspx?mfr=true
•
Protected EAP (PEAP)
•
LEAP
•
PEAP-GTC
•
EAP-FAST
Note
For more information about EAP authentication methods, see
Chapter 3, “Configuring EAP Types.”