10-2
Cisco Aironet 1400 Series Wireless Bridges Software Configuration Guide
OL-4059-01
Chapter 10 Configuring Authentication Types
Understanding Authentication Types
Understanding Authentication Types
This section describes the authentication types that you can configure on the bridge. The authentication
types are tied to the SSID that you configure on the bridge.
Before bridges can communicate, they must authenticate to each other using open or shared-key
authentication. For maximum security, bridges should also authenticate to your network using EAP
authentication, an authentication type that relies on an authentication server on your network.
The bridge uses four authentication mechanisms or types and can use more than one at the same time.
These sections explain each authentication type:
•
Open Authentication to the Bridge, page 10-2
•
Shared Key Authentication to the Bridge, page 10-2
•
EAP Authentication to the Network, page 10-3
Open Authentication to the Bridge
Open authentication allows any 1400 series bridge to authenticate and then attempt to communicate with
another 1400 series bridge. Using open authentication, a non-root bridge can authenticate to a root
bridge, but the non-root bridge can communicate only if its WEP keys match the root bridge’s. A bridge
that is not using WEP does not attempt to authenticate with a bridge that is using WEP. Open
authentication does not rely on a RADIUS server on your network.
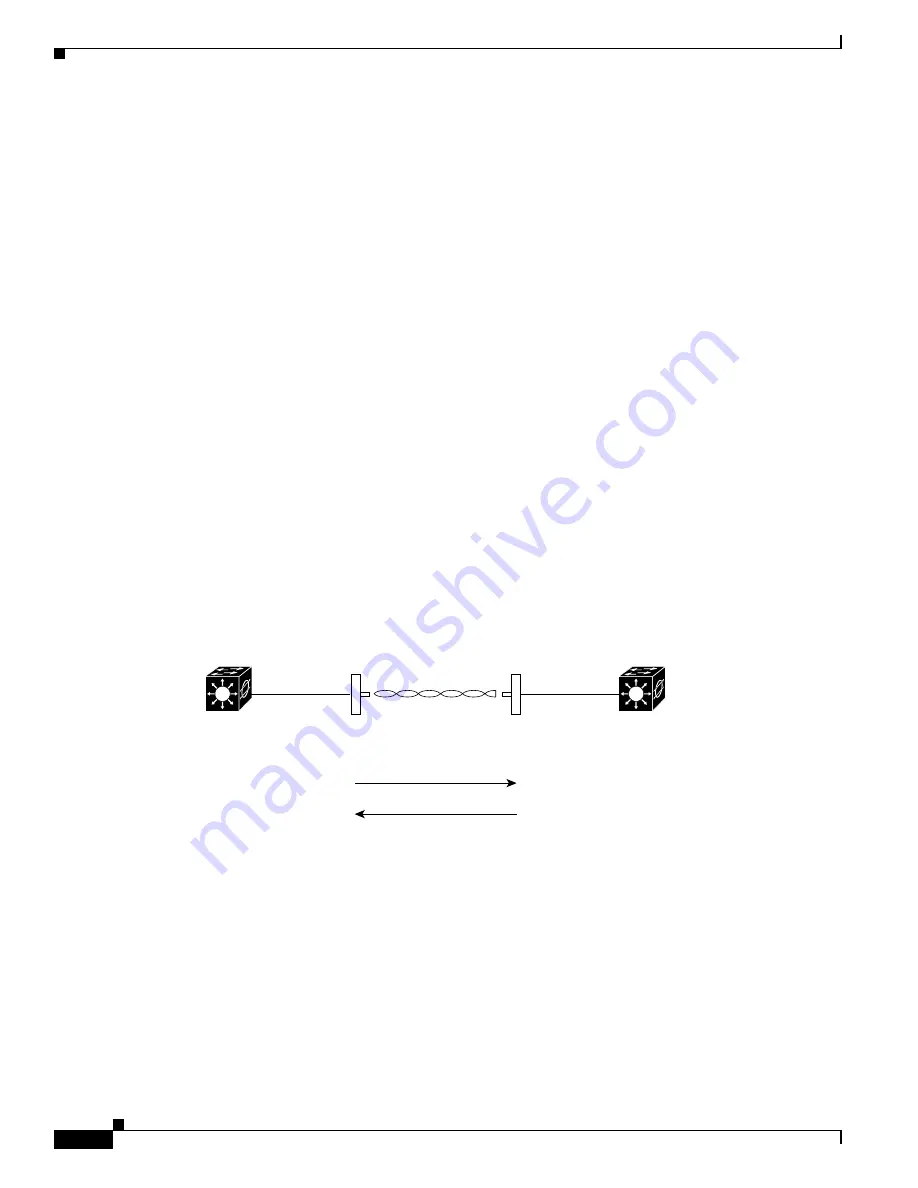
Figure 10-1
shows the authentication sequence between a non-root bridge trying to authenticate and a
root bridge using open authentication. In this example, the device’s WEP key does not match the bridge’s
key, so it can authenticate but not pass data.
Figure 10-1 Sequence for Open Authentication
Shared Key Authentication to the Bridge
Cisco provides shared key authentication to comply with the IEEE 802.11b standard. However, because
of shared key’s security flaws, we recommend that you avoid using it.
During shared key authentication, the root bridge sends an unencrypted challenge text string to other
bridges attempting to communicate with the root bridge. The bridge requesting authentication encrypts
the challenge text and sends it back to the root bridge. If the challenge text is encrypted correctly, the
root bridge allows the requesting device to authenticate. Both the unencrypted challenge and the
encrypted challenge can be monitored, however, which leaves the root bridge open to attack from an
88902
Switch on
LAN 1
1. Authentication request
Switch on
LAN 2
Non-Root Bridge
with
WEP key = 321
Root Bridge
with
WEP key = 123
2. Authentication response
















































