5-20
Cisco Aironet 1400 Series Wireless Bridges Software Configuration Guide
OL-4059-01
Chapter 5 Administering the Bridge
Managing the System Time and Date
Default NTP Configuration
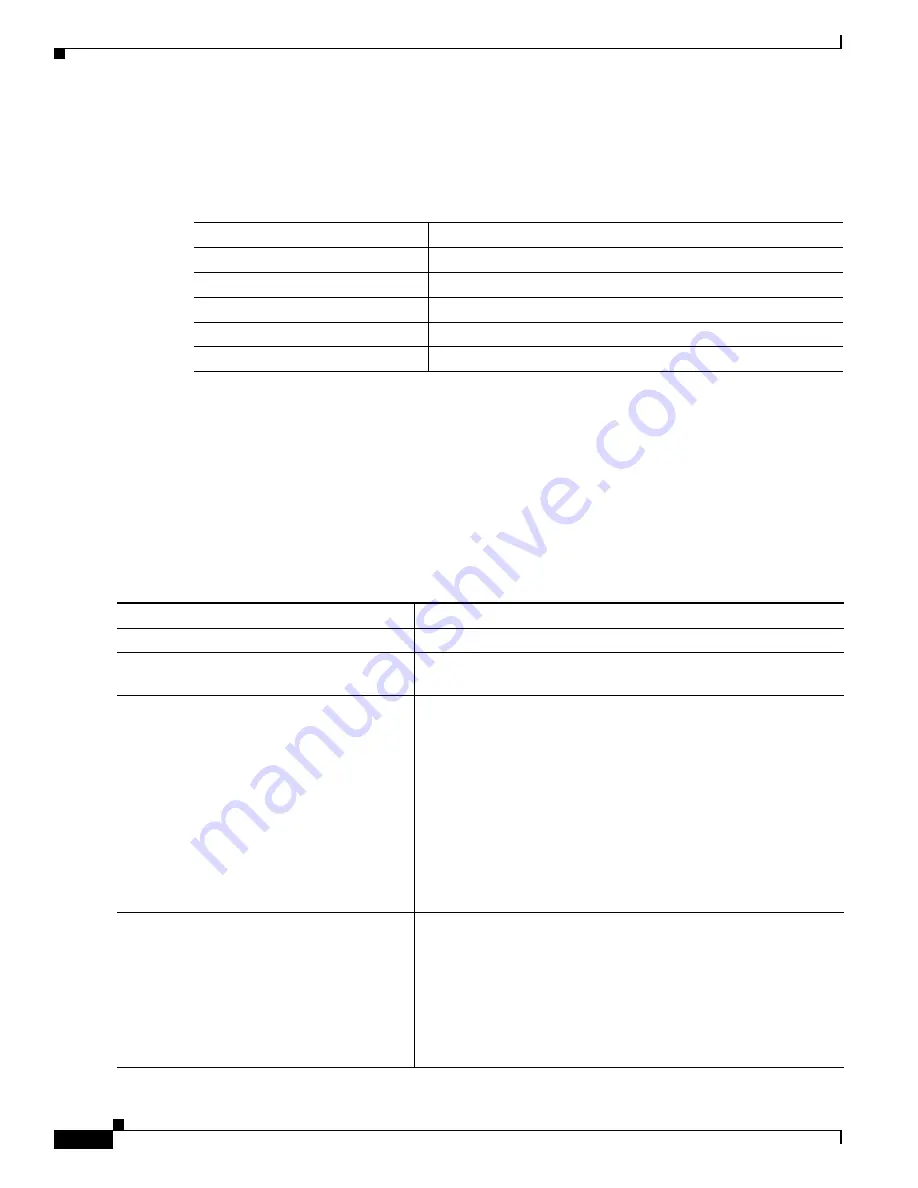
Table 5-2
shows the default NTP configuration.
NTP is disabled by default.
Configuring NTP Authentication
This procedure must be coordinated with the administrator of the NTP server; the information you configure
in this procedure must be matched by the servers used by the bridge to synchronize its time to the NTP server.
Beginning in privileged EXEC mode, follow these steps to authenticate the associations (communications
between devices running NTP that provide for accurate timekeeping) with other devices for security
purposes:
Table 5-2
Default NTP Configuration
Feature
Default Setting
NTP authentication
Disabled. No authentication key is specified.
NTP peer or server associations
None configured.
NTP broadcast service
Disabled; no interface sends or receives NTP broadcast packets.
NTP access restrictions
No access control is specified.
NTP packet source IP address
The source address is determined by the outgoing interface.
Command
Purpose
Step 1
configure terminal
Enter global configuration mode.
Step 2
ntp authenticate
Enable the NTP authentication feature, which is disabled by
default.
Step 3
ntp authentication-key
number
md5
value
Define the authentication keys. By default, none are defined.
•
For
number
, specify a key number. The range is 1 to
4294967295.
•
md5
specifies that message authentication support is provided
by using the message digest algorithm 5 (MD5).
•
For
value
, enter an arbitrary string of up to eight characters for
the key.
The bridge does not synchronize to a device unless both have one
of these authentication keys, and the key number is specified by the
ntp trusted-key
key-number
command.
Step 4
ntp trusted-key
key-number
Specify one or more key numbers (defined in Step 3) that a peer
NTP device must provide in its NTP packets for this bridge to
synchronize to it.
By default, no trusted keys are defined.
For
key-number
, specify the key defined in Step 3.
This command provides protection against accidentally
synchronizing the bridge to a device that is not trusted.
















































