10-16
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 10 NAT Examples and Reference
NAT for VPN
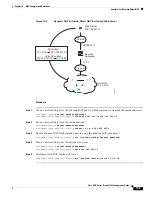
Figure 10-13
Interface PAT for Internet-Bound VPN Traffic (Intra-Interface)
The following figure shows a VPN client that wants to access an inside mail server. Because the ASA
expects traffic between the inside network and any outside network to match the interface PAT rule you
set up for Internet access, traffic from the VPN client (10.3.3.10) to the SMTP server (10.1.1.6) will be
dropped due to a reverse path failure: traffic from 10.3.3.10 to 10.1.1.6 does not match a NAT rule, but
returning traffic from 10.1.1.6 to 10.3.3.10
should
match the interface PAT rule for outgoing traffic.
Because forward and reverse flows do not match, the ASA drops the packet when it is received. To avoid
this failure, you need to exempt the inside-to-VPN client traffic from the interface PAT rule by using an
identity NAT rule between those networks. Identity NAT simply translates an address to the same
address.
VPN Client
209.165.201.10
Internet
S
rc: 209.165.201.10
10.
3
.
3
.10
20
3
.0.11
3
.1:6070
10.
3
.
3
.10
10.1.1.6
www.example.com
Inside
209.165.201.10
1.
HTTP request to www.example.com
4.
HTTP request to
www.example.com
C.
HTTP request to www.example.com
2.
ASA decrypts packet; src address is
now local address
S
rc: 20
3
.0.11
3
.1:6070
ASA Outside IP: 20
3
.0.11
3
.1
10.1.1.6
20
3
.0.11
3
.1:6075
S
rc: 10.1.1.6
A.
HTTP to
www.example.com
B.
ASA performs interface PAT for
outgoing traffic.
S
rc: 20
3
.0.11
3
.1:6075
3
.
ASA performs interface PAT for outgoing traffic.
Intra-interface config req’d.
3
0
3
462
Summary of Contents for ASA 5508-X
Page 11: ...P A R T 1 Access Control ...
Page 12: ......
Page 157: ...P A R T 2 Network Address Translation ...
Page 158: ......
Page 233: ...P A R T 3 Service Policies and Application Inspection ...
Page 234: ......
Page 379: ...P A R T 4 Connection Management and Threat Detection ...
Page 380: ......