5-7
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 5 Identity Firewall
Guidelines for the Identity Firewall
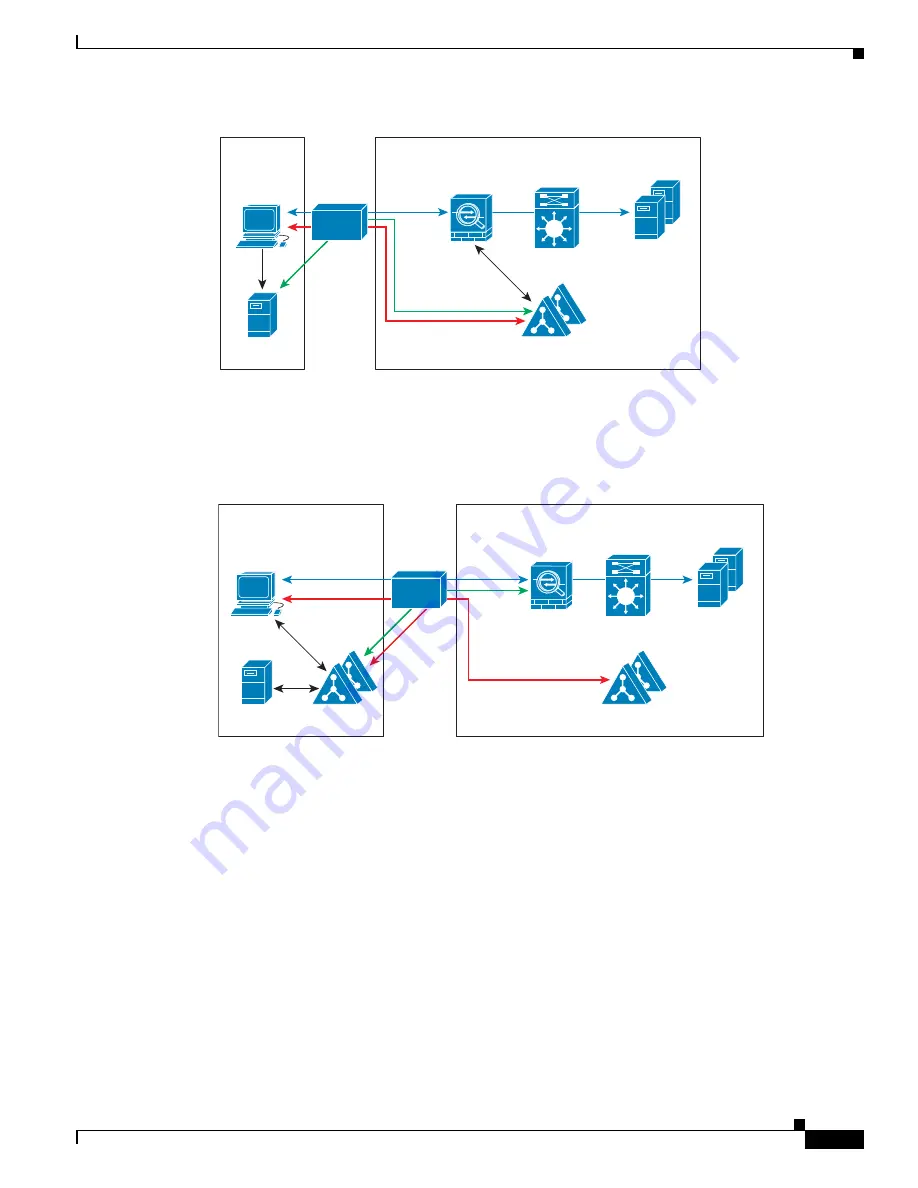
Figure 5-6
WAN-based Deployment with Remote AD Agent
The following figure shows an expanded remote site installation. An AD Agent and Active Directory
servers are installed at the remote site. The clients access these components locally when logging into
network resources located at the main site. The remote Active Directory server must synchronize its data
with the central Active Directory servers located at the main site.
Figure 5-7
WAN-based Deployment with Remote AD Agent and AD Servers
Guidelines for the Identity Firewall
This section describes the guidelines and limitations that you should check before configuring the
Identity Firewall.
Failover
•
The Identity Firewall supports user identity-IP address mapping and AD Agent status replication
from active to standby when Stateful Failover is enabled. However, only user identity-IP address
mapping, AD Agent status, and domain status are replicated. User and user group records are not
replicated to the standby ASA.
•
When failover is configured, the standby ASA must also be configured to connect to the AD Agent
directly to retrieve user groups. The standby ASA does not send NetBIOS packets to clients even
when the NetBIOS probing options are configured for the Identity Firewall.
Client
ASA
AD Servers
AD Agent
3
04006
Remote
S
ite
Enterpri
s
e Main
S
ite
RADIUS
mkg.example.com
10.1.1.2
WMI
Login/Authentication
LD
AP
WAN
Client
ASA
AD Servers
AD Servers
AD Agent
3
04007
Remote
S
ite
Enterpri
s
e Main
S
ite
RADIUS
mkg.example.com
10.1.1.2
LDAP
WMI
Directory Sync
WAN
Summary of Contents for ASA 5508-X
Page 11: ...P A R T 1 Access Control ...
Page 12: ......
Page 157: ...P A R T 2 Network Address Translation ...
Page 158: ......
Page 233: ...P A R T 3 Service Policies and Application Inspection ...
Page 234: ......
Page 379: ...P A R T 4 Connection Management and Threat Detection ...
Page 380: ......






























