6-4
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 6 ASA and Cisco TrustSec
About Cisco TrustSec
•
User identity and resource identity are retained throughout the Cisco TrustSec-capable switch
infrastructure.
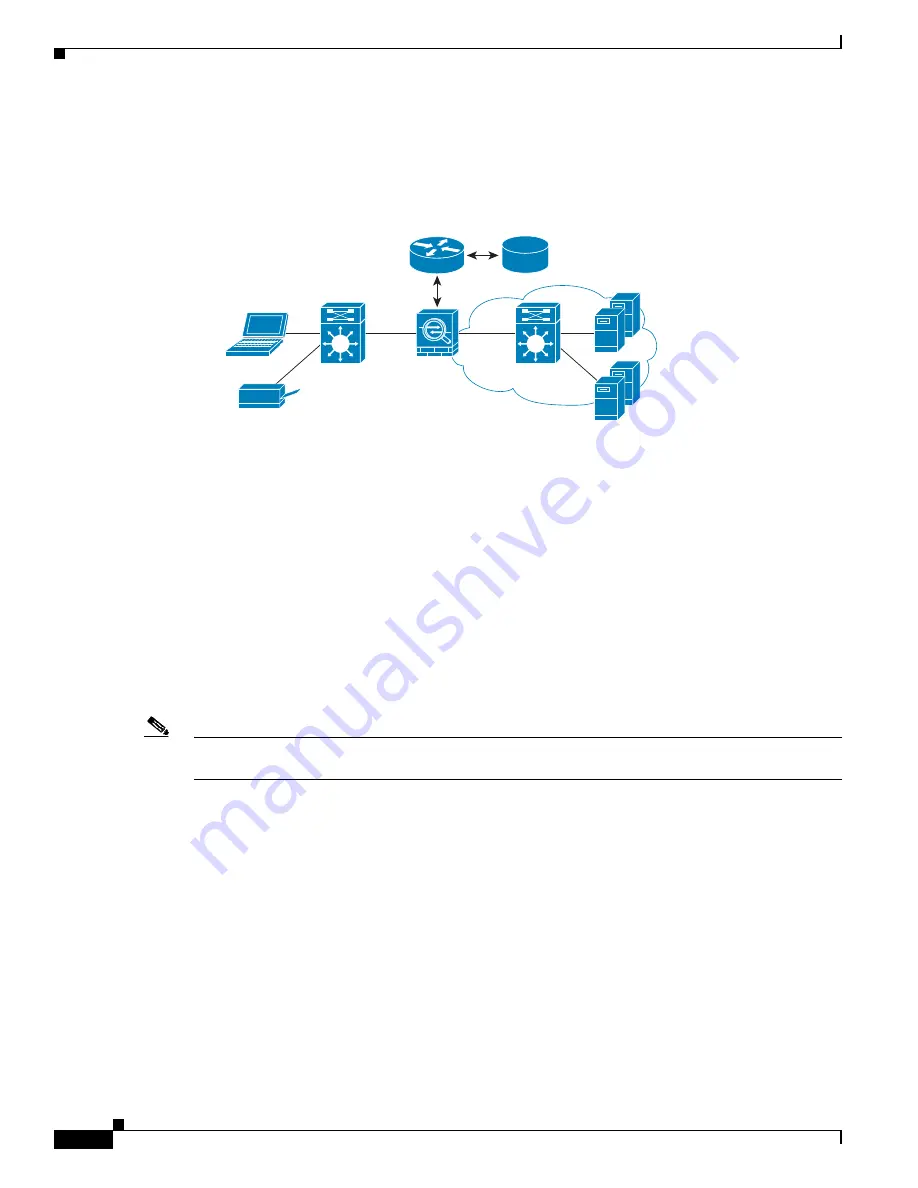
The following figure shows a deployment for security group name-based policy enforcement.
Figure 6-1
Security Group Name-Based Policy Enforcement Deployment
Implementing Cisco TrustSec allows you to configure security policies that support server segmentation
and includes the following features:
•
A pool of servers can be assigned an SGT for simplified policy management.
•
The SGT information is retained within the infrastructure of Cisco TrustSec-capable switches.
•
The ASA can use the IP-SGT mapping for policy enforcement across the Cisco TrustSec domain.
•
Deployment simplification is possible because 802.1x authorization for servers is mandatory.
How the ASA Enforces Security Group-Based Policies
Note
User-based security policies and security-group based policies can coexist on the ASA. Any combination
of network, user-based, and security-group based attributes can be configured in a security policy.
To configure the ASA to function with Cisco TrustSec, you must import a Protected Access Credential
(PAC) file from the ISE.
Importing the PAC file to the ASA establishes a secure communication channel with the ISE. After the
channel is established, the ASA initiates a PAC secure RADIUS transaction with the ISE and downloads
Cisco TrustSec environment data (that is, the security group table). The security group table maps SGTs
to security group names. Security group names are created on the ISE and provide user-friendly names
for security groups.
The first time that the ASA downloads the security group table, it walks through all entries in the table
and resolves all the security group names included in security policies that have been configured on it;
then the ASA activates those security policies locally. If the ASA cannot resolve a security group name,
it generates a syslog message for the unknown security group name.
ASA
End Points
(Access Requestors)
Access
Switch
Access
Switch
3
04015
SXP
SXP
Mktg servers
Corp servers
Summary of Contents for ASA 5508-X
Page 11: ...P A R T 1 Access Control ...
Page 12: ......
Page 157: ...P A R T 2 Network Address Translation ...
Page 158: ......
Page 233: ...P A R T 3 Service Policies and Application Inspection ...
Page 234: ......
Page 379: ...P A R T 4 Connection Management and Threat Detection ...
Page 380: ......









































