12-6
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 12 Getting Started with Application Layer Protocol Inspection
Defaults for Application Inspection
•
Inspected protocols are subject to advanced TCP-state tracking, and the TCP state of these
connections is not automatically replicated. While these connections are replicated to the standby
unit, there is a best-effort attempt to re-establish a TCP state.
•
TCP/UDP Traffic directed to the ASA (to an interface) is inspected by default. However, ICMP
traffic directed to an interface is never inspected, even if you enable ICMP inspection. Thus, a ping
(echo request) to an interface can fail under specific circumstances, such as when the echo request
comes from a source that the ASA can reach through a backup default route.
Defaults for Application Inspection
The following topics explain the default operations for application inspection.
•
Default Inspections and NAT Limitations, page 12-6
•
Default Inspection Policy Maps, page 12-9
Default Inspections and NAT Limitations
By default, the configuration includes a policy that matches all default application inspection traffic and
applies inspection to the traffic on all interfaces (a global policy). Default application inspection traffic
includes traffic to the default ports for each protocol. You can only apply one global policy, so if you
want to alter the global policy, for example, to apply inspection to non-standard ports, or to add
inspections that are not enabled by default, you need to either edit the default policy or disable it and
apply a new one.
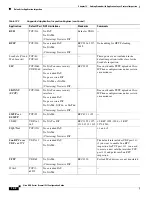
The following table lists all inspections supported, the default ports used in the default class map, and
the inspection engines that are on by default, shown in bold. This table also notes any NAT limitations.
In this table:
•
Inspection engines that are enabled by default for the default port are in bold.
•
The ASA is in compliance with the indicated standards, but it does not enforce compliance on
packets being inspected. For example, FTP commands are supposed to be in a particular order, but
the ASA does not enforce the order.
Table 12-1
Supported Application Inspection Engines
Application
Default Port NAT Limitations
Standards
Comments
CTIQBE
TCP/2748
No extended PAT.
No NAT64.
(Clustering) No static PAT.
—
—
DCERPC
TCP/135
No NAT64.
—
—
DNS
over UDP
UDP/53
No NAT support is available for
name resolution through
WINS.
RFC 1123
—
FTP
TCP/21
(Clustering) No static PAT.
RFC 959
—
GTP
UDP/3386
UDP/2123
No extended PAT.
No NAT.
—
Requires a special license.
Summary of Contents for ASA 5508-X
Page 11: ...P A R T 1 Access Control ...
Page 12: ......
Page 157: ...P A R T 2 Network Address Translation ...
Page 158: ......
Page 233: ...P A R T 3 Service Policies and Application Inspection ...
Page 234: ......
Page 379: ...P A R T 4 Connection Management and Threat Detection ...
Page 380: ......