14-4
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 14 ASA and Cisco Cloud Web Security
Licensing Requirements for Cisco Cloud Web Security
–
For the default username, it is sent in the following format:
[
domain-name
\]
username
For example, if you configure the default username to be “Guest,” then the ASA sends “Guest.”
If you configure the default username to be “Cisco\Guest,” then the ASA sends “Cisco\Guest.”
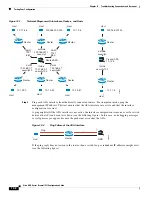
How Groups and the Authentication Key Interoperate
Unless you need the per-ASA policy that a custom group plus group key provides, you will likely use a
company key. Note that not all custom groups are associated with a group key. You can use non-keyed
custom groups to identify IP addresses or usernames, and use them in your policy along with rules that
use directory groups.
Even if you do want per-ASA policy and are using a group key, you can also use the matching capability
provided by directory groups and non-keyed custom groups. In this case, you might want an ASA-based
policy, with some exceptions based on group membership, IP address, or username. For example, if you
want to exempt users in the America\Management group across all ASAs:
1.
Add a directory group for America\Management.
2.
Add an exempt rule for this group.
3.
Add rules for each custom group plus group key after the exempt rule to apply policy per-ASA.
4.
Traffic from users in America\Management will match the exempt rule, while all other traffic will
match the rule for the ASA from which it originated.
Many combinations of keys, groups, and policy rules are possible.
Failover from Primary to Backup Proxy Server
When you subscribe to the Cisco Cloud Web Security service, you are assigned a primary Cloud Web
Security proxy server and backup proxy server.
If any client is unable to reach the primary server, then the ASA starts polling the tower to determine
availability. (If there is no client activity, the ASA polls every 15 minutes.) If the proxy server is
unavailable after a configured number of retries (the default is 5; this setting is configurable), the server
is declared unreachable, and the backup proxy server becomes active.
After a failover to the backup server, the ASA continues to poll the primary server. If the primary server
becomes reachable, then the ASA returns to using the primary server.
You can also choose how the ASA handles web traffic when it cannot reach either the primary or backup
Cloud Web Security proxy server. It can block or allow all web traffic. By default, it blocks web traffic.
Licensing Requirements for Cisco Cloud Web Security
Model
License Requirement
ASAv
Standard or Premium License.
All other models
Strong Encryption (3DES/AES) License to encrypt traffic between the security appliance and the
Cloud Web Security server.
Summary of Contents for ASA 5512-X
Page 5: ...P A R T 1 Service Policies and Access Control ...
Page 6: ......
Page 51: ...P A R T 2 Network Address Translation ...
Page 52: ......
Page 127: ...P A R T 3 Application Inspection ...
Page 128: ......
Page 255: ...P A R T 4 Connection Settings and Quality of Service ...
Page 256: ......
Page 303: ...P A R T 5 Advanced Network Protection ...
Page 304: ......
Page 339: ...P A R T 6 ASA Modules ...
Page 340: ......