4-39
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 4 Network Address Translation (NAT
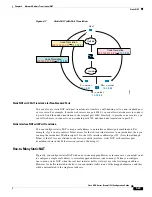
Identity NAT
Example
The following example maps a host address to itself using an inline mapped address:
hostname(config)#
object network my-host-obj1
hostname(config-network-object)#
host 10.1.1.1
hostname(config-network-object)#
nat (inside,outside) static 10.1.1.1
The following example maps a host address to itself using a network object:
hostname(config)#
object network my-host-obj1-identity
hostname(config-network-object)#
host 10.1.1.1
hostname(config-network-object)#
object network my-host-obj1
hostname(config-network-object)#
host 10.1.1.1
hostname(config-network-object)#
nat (inside,outside) static my-host-obj1-identity
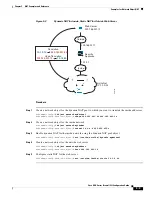
Configure Identity Twice NAT
This section describes how to configure an identity NAT rule using twice NAT.
Procedure
Step 1
Create host or range network objects (
object network
command), or network object groups
(
object-group network
command), for the source real addresses (you will typically use the same object
for the source mapped addresses), the destination real addresses, and the destination mapped addresses.
•
If you want to perform identity NAT for all addresses, you can skip creating an object for the source
real addresses and instead use the keywords
any any
in the
nat
command.
•
If you want to configure destination static interface NAT with port translation only, you can skip
adding an object for the destination mapped addresses, and instead specify the
interface
keyword
in the
nat
command.
If you do create objects, consider the following guidelines:
•
The mapped object or group can contain a host, range, or subnet.
•
The real and mapped source objects must match. You can use the same object for both, or you can
create separate objects that contain the same IP addresses.
Step 2
(Optional.) Create service objects for the:
•
Source
or
Destination real ports
•
Source
or
Destination mapped ports
A service object can contain both a source and destination port; however, you should specify
either
the
source
or
the destination port for both service objects. You should only specify
both
the source and
destination ports if your application uses a fixed source port (such as some DNS servers); but fixed
source ports are rare. For example, if you want to translate the port for the source host, then configure
the source service.
Step 3
Configure
identity NAT
.
nat
[
(
real_ifc
,
mapped_ifc
)
] [
line
| {
after-object
[
line
]}]
source static
{
nw_obj nw_obj
|
any
any
}
[
destination
static
{
mapped_obj
|
interface
[
ipv6
]}
real_obj
]
[
service
real_src_mapped_dest_svc_obj
mapped_src_real_dest_svc_obj
]
[
no-proxy-arp
] [
route-lookup
] [
inactive
] [
description
desc
]
Summary of Contents for ASA 5512-X
Page 5: ...P A R T 1 Service Policies and Access Control ...
Page 6: ......
Page 51: ...P A R T 2 Network Address Translation ...
Page 52: ......
Page 127: ...P A R T 3 Application Inspection ...
Page 128: ......
Page 255: ...P A R T 4 Connection Settings and Quality of Service ...
Page 256: ......
Page 303: ...P A R T 5 Advanced Network Protection ...
Page 304: ......
Page 339: ...P A R T 6 ASA Modules ...
Page 340: ......