PDN Gateway Overview
▀ Features and Functionality - Inline Service Support
▄ Cisco ASR 5000 Series Product Overview
OL-22938-02
subscribers through rulebase or APN/Subscriber configuration. The policy determines the action to be taken on the
content request on the basis of its category. A maximum of one policy can be associated with a rulebase.
ICAP Interface
Provides a value-added service to prevent unintended viewing of objectionable content that exploits underage children.
Content Filtering offers mobile operators a way to increase data ARPU and subscriber retention through a network-
based solution for parental controls and content filtering. The Content Filtering ICAP solution is appropriate for
operators with existing installations of Active Content Filtering servers in their networks.
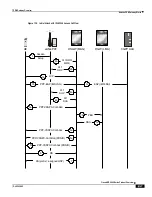
The Enhanced Charging Service (ECS) for the P-GW provides a streamlined Internet Content Adaptation Protocol
(ICAP) interface to leverage the Deep Packet Inspection (DPI) to enable external Application Servers to provide their
services without performing the DPI functionality and without being inserted in the data flow. The ICAP interface may
be attractive to mobile operators that prefer to use an external Active Content Filtering (ACF) Platform. If a subscriber
initiates a WAP (WAP1.x or WAP2.0) or Web session, the subsequent GET/POST request is detected by the deep
packet inspection function. The URL of the GET/POST request is extracted by the local DPI engine on the ASR 5000
platform and passed, along with subscriber identification information and the subscriber request, in an ICAP message to
the Application Server (AS). The AS checks the URL on the basis of its category and other classifications like, type,
access level, content category and decides if the request should be authorized, blocked or redirected by answering the
GET/POST message. Depending upon the response received from the ACF server, the P-GW either passes the request
unmodified or discards the message and responds to the subscriber with the appropriate redirection or block message.
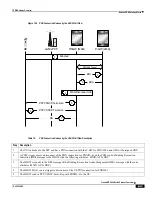
Peer-to-Peer Detection
Allows operators to identify P2P traffic in the network and applying appropriate controlling functions to ensure fair
distribution of bandwidth to all subscribers.
Peer-to-Peer (P2P) is a term used in two slightly different contexts. At a functional level, it means protocols that interact
in a peering manner, in contrast to client-server manner. There is no clear differentiation between the function of one
node or another. Any node can function as a client, a server, or both—a protocol may not clearly differentiate between
the two. For example, peering exchanges may simultaneously include client and server functionality, sending and
receiving information.
Detecting peer-to-peer protocols requires recognizing, in real time, some uniquely identifying characteristic of the
protocols. Typical packet classification only requires information uniquely typed in the packet header of packets of the
stream(s) running the particular protocol to be identified. In fact, many peer-to-peer protocols can be detected by simple
packet header inspection. However, some P2P protocols are different, preventing detection in the traditional manner.
This is designed into some P2P protocols to purposely avoid detection. The creators of these protocols purposely do not
publish specifications. A small class of P2P protocols is stealthier and more challenging to detect. For some protocols
no set of fixed markers can be identified with confidence as unique to the protocol.
Operators care about P2P traffic because of the behavior of some P2P applications (for example, Bittorrent, Skype, and
eDonkey). Most P2P applications can hog the network bandwidth such that 20% P2P users can generate as much as
traffic generated by the rest 80% non-P2P users. This can result into a situation where non-P2P users may not get
enough network bandwidth for their legitimate use because of excess usage of bandwidth by the P2P users. Network
operators need to have dynamic network bandwidth / traffic management functions in place to ensure fair distributions
of the network bandwidth among all the users. And this would include identifying P2P traffic in the network and
applying appropriate controlling functions to the same (for example, content-based premium billing, QoS modifications,
and other similar treatments).
Summary of Contents for ASR 5000 Series
Page 1: ......
Page 26: ......
Page 48: ...New In Release 10 0 SCM Features Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Page 50: ......
Page 58: ......
Page 68: ......
Page 126: ......
Page 138: ......
Page 146: ......
Page 218: ......
Page 236: ......
Page 356: ......
Page 374: ......
Page 422: ......
Page 496: ......
Page 572: ......
Page 654: ......
Page 700: ......
Page 726: ......
Page 784: ......
Page 816: ......
Page 844: ......
Page 906: ......
Page 926: ......
Page 942: ......
Page 943: ...Cisco ASR 5000 Series Product Overview OL 22938 02 Chapter 30 Technical Specifications ...
Page 966: ......
Page 972: ......