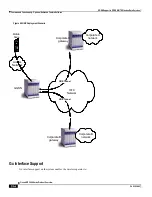
GGSN Support in GPRS/UMTS Wireless Data Services
▀ Features and Functionality - Base Software
▄ Cisco ASR 5000 Series Product Overview
OL-22938-02
RFC-2328, OSPF Version 2, April 1998
RFC-3101 OSPF-NSSA Option, January 2003
Border Gateway Protocol version 4 (BGP-4)
: The system supports a subset of BGP (RFC-1771, A Border
Gateway Protocol 4 (BGP-4)), suitable for eBGP support of multi-homing typically used to support
geographically redundant mobile gateways, is supported.
EBGP is supported with multi-hop, route filtering, redistribution, and route maps. The network command is
support for manual route advertisement or redistribution.
BGP route policy and path selection is supported by the following means:
Prefix match based on route access list
AS path access-list
Modification of AS path through path prepend
Origin type
MED
Weight
Route Policy
: Routing policies modify and redirect routes to and from the system to satisfy specific routing
needs. The following methods are used with or without active routing protocols (i.e. static or dynamic routing)
to prescribe routing policy:
Route Access Lists
: The basic building block of a routing policy, route access lists filter routes based
upon a specified range of IP addresses.
IP Prefix Lists
: A more advanced element of a routing policy. An IP Prefix list filters routes based
upon IP prefixes
AS Path Access Lists
: A basic building block used for Border Gateway Protocol (BGP) routing, these
lists filter Autonomous System (AS) paths.
Route Maps
: Route-maps are used for detailed control over the manipulation of routes during route selection or
route advertisement by a routing protocol and in route redistribution between routing protocols. This detailed
control is achieved using IP Prefix Lists, Route Access Lists and AS Path Access Lists to specify IP addresses,
address ranges, and Autonomous System Paths.
Equal Cost Multiple Path (ECMP)
: ECMP allows distribution of traffic across multiple routes that have the
same cost to the destination. In this manner, throughput load is distributed across multiple path, typically to
lessen the burden on any one route and provide redundancy. The mobile gateway supports from four to ten
equal-cost paths.
Important:
For more information on IP Routing configuration, refer
Routing
chapter in
System Enhanced
Feature Configuration Guide
.
Support of Charging Characteristics Provided by AAA Server
This feature provides the ability for operators to apply Charging Characteristics (CC) from the AAA server instead of a
hard coded local profile during access authentication.
The RADIUS attribute
3GPP-Chrg-Char
can be used to get the charging characteristics from RADIUS in Access-
Accept message. Accepting the RADIUS returned charging characteristic profile must be enabled per APN. The CC
Summary of Contents for ASR 5000 Series
Page 1: ......
Page 26: ......
Page 48: ...New In Release 10 0 SCM Features Cisco ASR 5000 Series Product Overview OL 22938 02 ...
Page 50: ......
Page 58: ......
Page 68: ......
Page 126: ......
Page 138: ......
Page 146: ......
Page 218: ......
Page 236: ......
Page 356: ......
Page 374: ......
Page 422: ......
Page 496: ......
Page 572: ......
Page 654: ......
Page 700: ......
Page 726: ......
Page 784: ......
Page 816: ......
Page 844: ......
Page 906: ......
Page 926: ......
Page 942: ......
Page 943: ...Cisco ASR 5000 Series Product Overview OL 22938 02 Chapter 30 Technical Specifications ...
Page 966: ......
Page 972: ......