6-14
Firepower 7000 Series Hardware Installation Guide
Chapter 6 Deploying Firepower Managed Devices
Deployment Options
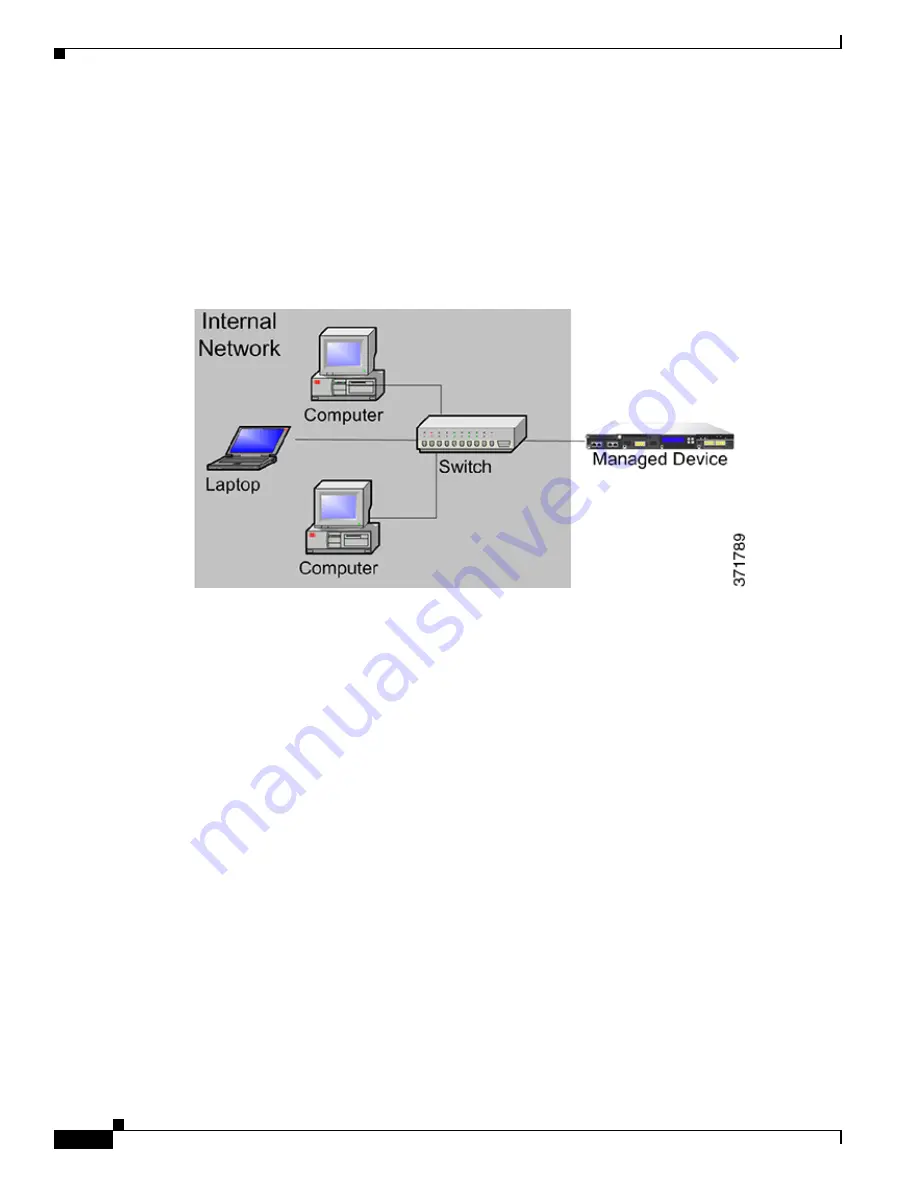
On the Internal Network
A malicious attack can originate from a computer on your internal network. This can be a deliberate act
(for example, an unknown computer appears unexpectedly on your network), or an accidental infection
(for example, a work laptop infected off-site is connected to the network and spreads a virus). Risk on
the internal network can also be outbound (for example, a computer sends information to a suspicious
external IP address).
This dynamic network requires a strict access control policy for all internal traffic in addition to
outbound traffic. Add access control rules to tightly control traffic between users and applications.
On the Core Network
Core assets are those assets critical to the success of your business that must be protected at all cost.
Although core assets vary depending on the nature of your business, typical core assets include financial
and management centers or intellectual property repositories. If the security on the core assets is
breached, your business can be destroyed.
Although this segment must be readily available for your business to function, it must be tightly
restricted controlled. Access control should ensure that these assets cannot be reached by those network
segments with the highest risk, such as remote networks or mobile devices. Always use the most
aggressive control on this segment, with strict rules for user and application access.






































