Appendix D
Regulatory Information
36
Dual-Band Wireless-N Gigabit Router
Wireless Equipment
(Wireless-N/G/A/B Products)
The following standards were applied during the
assessment of the product against the requirements of
the Directive 1999/5/EC:
Radio: EN 300 328 and/or EN 301 893 as applicable
•
EMC: EN 301 489-1, EN 301 489-17
•
Safety: EN 60950 and either EN 50385 or EN 50371
•
Dynamic Frequency Selection (DFS) and Transmit Power
Control (TPC) are required for operation in the 5 GHz
band.
DFS: The equipment meets the DFS requirements as
defined in ETSI EN 301 893. This feature is required by
the regulations to avoid interference with Radio Location
Services (radars).
TPC: For operation in the 5 GHz band, the maximum power
level is 3 dB or more below the applicable limit. As such,
TPC is not required.
CE Marking
For the Linksys Wireless-N, -G, -B, and/or -A products,
the following CE mark, notified body number (where
applicable), and class 2 identifier are added to the
equipment.
or
or
or
Check the CE label on the product to find out which
notified body was involved during the assessment.
National Restrictions
This product may be used in all EU countries (and other
countries following the EU directive 1999/5/EC) without
any limitation except for the countries mentioned below:
Ce produit peut être utilisé dans tous les pays de l’UE (et dans
tous les pays ayant transposés la directive 1999/5/CE) sans
aucune limitation, excepté pour les pays mentionnés ci-
dessous:
Questo prodotto è utilizzabile in tutte i paesi EU (ed in tutti
gli altri paesi che seguono le direttive EU 1999/5/EC) senza
nessuna limitazione, eccetto per i paesi menzionati di
seguito:
Das Produkt kann in allen EU Staaten ohne Einschränkungen
eingesetzt werden (sowie in anderen Staaten die der EU
Direktive 1999/5/CE folgen) mit Außnahme der folgenden
aufgeführten Staaten:
In the majority of the EU and other European countries,
the 2.4- and 5-GHz bands have been made available for
the use of wireless local area networks (LANs). The table
labelled "Overview of Regulatory Requirements for
Wireless LANs" provides an overview of the regulatory
requirements applicable for the 2.4- and 5-GHz bands.
Later in this document you will find an overview of
countries in which additional restrictions or requirements
or both are applicable.
The requirements for any country may evolve. Linksys
recommends that you check with the local authorities for
the latest status of their national regulations for both the
2.4- and 5-GHz wireless LANs.
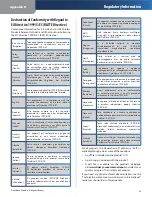
Overview of Regulatory Requirements for Wireless LANs
Frequency
Band (MHz)
Max Power Level
(EIRP) (mW)
Indoor
ONLY
Indoor &
Outdoor
2400-2483.5
100
X
5150-5350
†
200
X
5470-5725
†
1000
X
Dynamic Frequency Selection and Transmit Power Control are
†
required in the frequency ranges of 5250-5350 MHz and 5470-5725
MHz.
The following countries have restrictions and/or
requirements in addition to those given in the table
labelled "Overview of Regulatory Requirements for
Wireless LANs":
Denmark
In Denmark, the band 5150 - 5350 MHz is also allowed for
outdoor usage.
I Danmark må frekvensbåndet 5150 - 5350 også anvendes
udendørs.