1-9
Firepower 7000 and 8000 Series Installation Guide
Chapter 1 Introduction to the Firepower System
Firepower System Components
Firepower System Components
The sections that follow describe some of the key capabilities of the Firepower System that contribute
to your organization’s security, acceptable use policy, and traffic management strategy.
Tip
Many Firepower System capabilities are appliance model, license, and user role dependent. Where
needed, Firepower System documentation outlines the requirements for each feature and task.
Redundancy and Resource Sharing
The redundancy and resource-sharing features of the Firepower System allow you to ensure continuity
of operations and to combine the processing resources of multiple physical devices:
•
Device stacking allows you to increase the amount of traffic inspected on a network segment by
connecting two to four physical devices in a stacked configuration.
•
Device high availability allows you to establish redundancy of networking functionality and
configuration data between two or more 7000 and 8000 Series devices or stacks.
Multiple Management Interfaces
You can use
multiple management interfaces
on a Firepower Management Center, device, or both, to
improve performance by separating traffic into two traffic channels: the
management traffic channel
carries inter-device communication and the
event traffic channel
carries high volume event traffic such
as intrusion events. Both traffic channels can be carried on the same management interface or split
between two management interfaces, each interface carrying one traffic channel.
You can also create a route from a specific management interface on your Firepower Management Center
to a different network, allowing your Firepower Management Center to isolate and manage device traffic
on one network separately from device traffic on another network.
Additional management interfaces have many of the same capabilities as the default management
interface with the following exceptions:
•
You can configure DHCP on the default (
eth0
) management interface only. Additional (
eth1
and so
on) interfaces require unique static IP addresses and hostnames.
•
You must configure both traffic channels to use the same non-default management interface when
your Firepower Management Center and managed device are separated by a NAT device.
•
You can use Lights-Out Management on the default management interface only.
•
On the 70xx Family, you can separate traffic into two channels and configure those channels to send
traffic to one or more management interfaces on the Firepower Management Center. However,
because the 70xx Family contains only one management interface, the device receives traffic sent
from the Firepower Management Center on only one management interface.
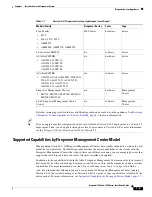
8350, 8360, 8370, 8390
(AC or DC power)
PG35-2U-AC/DC
AMP830, AMP8360, AMP8370, AMP8390
(AC or DC power)
PG35-2U-AC/DC
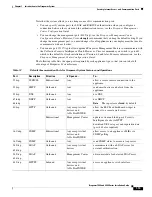
Table 1-5
8000 Series Chassis Models (continued)
Firepower and AMP Device Model
Hardware Chassis Code