A-13
Firepower 7000 and 8000 Series Installation Guide
Appendix A Power Requirements for Firepower Devices
Firepower and AMP 83xx Family Appliances
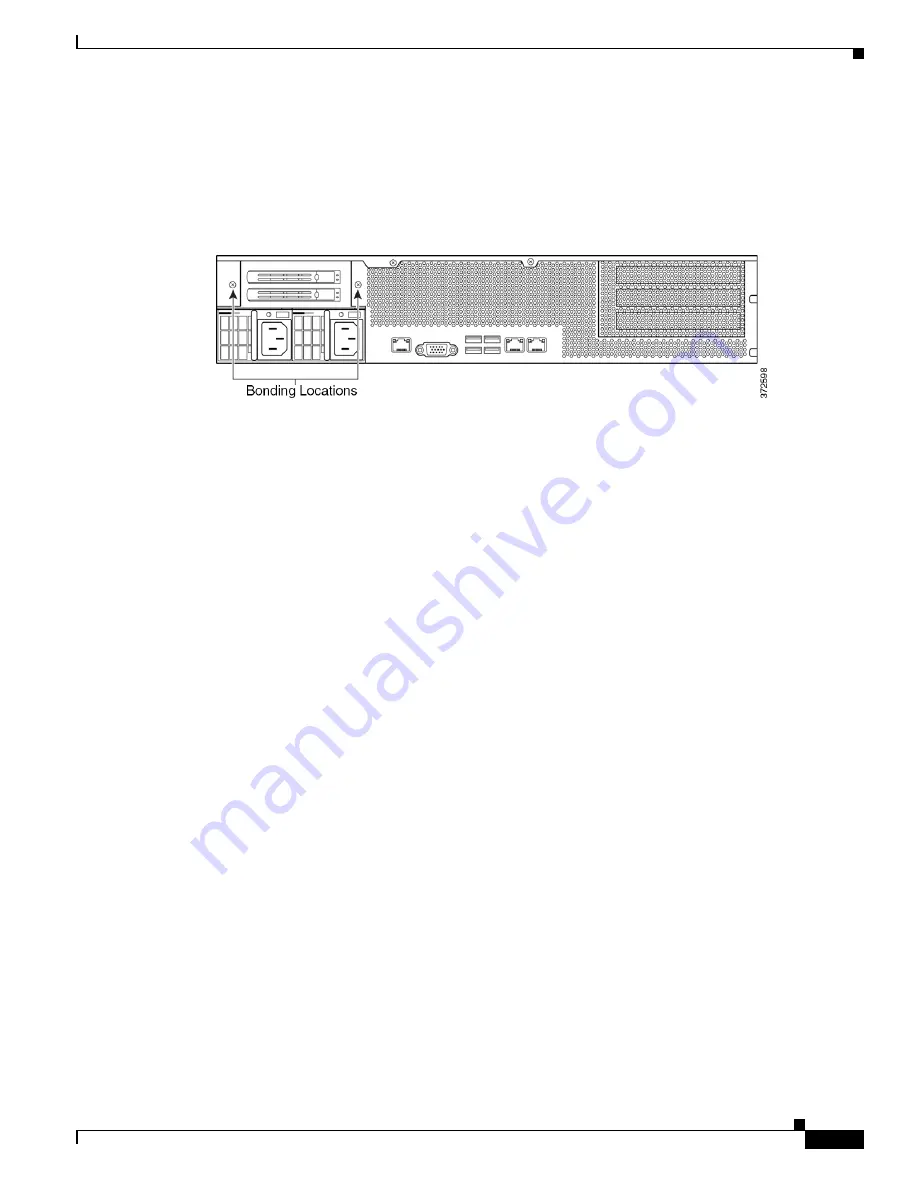
Bonding Locations
Ground bonding locations are provided on the rear of the chassis. M4 studs are provided.
Outside-toothed lock washers are provided for attaching ring terminals. A standard ground symbol is
available by each stud.
The following illustration indicates the bonding locations on the 2U chassis.
Recommended Terminals
You must use UL-Approved terminals for the ground connection. Ring terminals with a clearance hole
for 4mm or #8 studs may be used. For 10-12 AWG wire, Tyco 34853 is recommended. This is a
UL-approved, ring terminal with a hole for a #8 stud.
Ground Wire Requirements
The ground wire must be sized sufficiently to handle the current of the circuit in case of a single fault.
The size of the ground wire should be equal to the current of the breaker used to protect the circuit. For
AC circuits, see
. For DC currents, see
.
Bare conductors must be coated with antioxidant before crimp connections are made. Only copper cables
can be used for grounding purposes.
DC Supplies
The DC power supplies have additional ground connections on each supply. This allows the
hot-swappable supply to be connected to power, return and ground so that it may be safely inserted. This
ground lug must be attached.
It is a M4 screw with an outside-toothed lock washer screw.
The ground wire should be sized to match the breaker for the circuit.
Firepower and AMP 83xx Family Appliances
This section describes the power requirements for:
•
Firepower and AMP 8350, 8360, 8370, and 8390 (PG35-2U-AC/DC)
These appliances are suitable for installation by qualified personnel in network telecommunication
facilities and locations where the National Electric Code applies.
Cisco recommends that you save the packing materials in case a return is necessary.
For more information, see the following sections:
















































