Configuring delegated credential checking (SIP only)
By default, the VCS uses the relevant credential checking mechanisms (local database, Active Directory
Service or H.350 directory via LDAP) on the same VCS that is performing the authentication challenge.
Alternatively you can configure the VCS that is performing the authentication challenges to delegate the
credential checking of SIP messages, via a traversal zone, to another VCS (typically a VCS Control).
Delegated credential checking is useful in deployments where you want to allow devices to register on the
VCS Expressway (so that, for example, calls may be made without having to use a traversal license), but for
security you want all communications with authentication systems (such as an Active Directory server) to be
performed inside the enterprise.
n
Credential checking for both SIP Digest and NTLM messages may be delegated.
n
All messages must be for locally-defined SIP domains. You can delegate credential checking to different
traversal clients on a per domain basis if required.
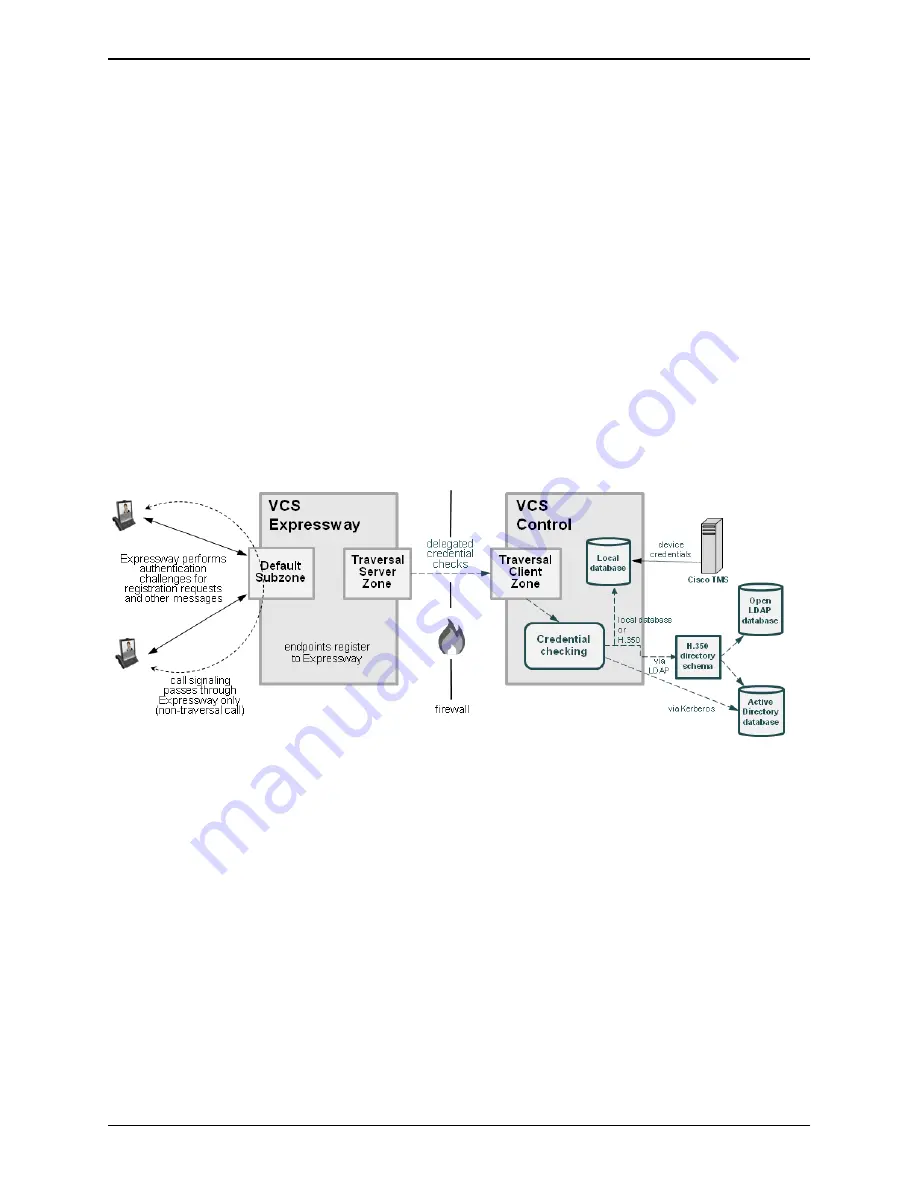
The following diagram shows how incoming SIP messages (calls, registrations and so on) are challenged by
the VCS Expressway, but the checking of the credentials presented in response to those challenges is
delegated to the VCS Control.
Configuring your video communications network for delegated
credential checking
Several configuration steps are involved, on both your VCS Expressway and your VCS Control, in setting up
your video network for delegated credential checking.
It is likely that much of this configuration, such as the set of local SIP domains, will already be in place,
however the sections below list all of the necessary configuration requirements.
VCS Expressway and VCS Control
There must be a secure traversal zone connection between the VCS Control and the VCS Expressway:
n
The traversal client zone and the traversal server zone must be configured to use SIP TLS with
TLS verify
mode
set to
On
, and
Media encryption mode
must be
Force encrypted
.
n
Both VCSs must trust each other's server certificate. As each VCS acts both as a client and as a server
you must ensure that each VCS’s certificate is valid both as a client and as a server.
n
If a H.323 or a non-encrypted connection is required, a separate pair of traversal zones must be configured.
Cisco VCS Administrator Guide (X8.1.1)
Page 109 of 507
Device authentication
About device authentication