Practical configuration of authentication policy
VCS Control
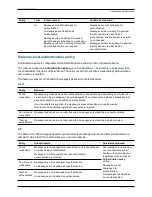
The table below contains practical guidelines for configuring authentication policy on a VCS Control.
Authentication point
Guideline
Default Zone
Use
Check credentials
.
Default Subzone
Use
Check credentials
.
Specific local subzones
For known local subnets, to avoid having to configure all local endpoints with
credentials, use
Treat as authenticated
.
Although this is a practical solution, we recommend that no
Treat as
authenticated
subzones are used, and that every endpoint is populated with
appropriate and unique credentials and that
Check credentials
is used.
Other subzones
Use
Check credentials
.
Traversal zone
Use
Check credentials
. Always check the credentials of requests coming from
the VCS Expressway.
Neighbor zone
Use
Do not check credentials
and set
SIP authentication trust mode
to
On
.
VCS Expressway
Ideally, VCS Expressway authentication policy, should follow exactly the same guidelines as for the VCS
Control. However if AD Direct or H.350 access is required, many security policies will not allow a device in a
DMZ access to those resources. Practicality therefore recommends that authentication is left to the VCS
Control. For SIP devices you can use
delegated credential checking
; this allows SIP devices to register to
the VCS Expressway but be authenticated via a device authentication mechanism configured on the VCS
Control.
You can also use
registration allow and deny lists
to limit what can register to the VCS Expressway. If it is
required that outbound calls may only be made by authenticated users, ensure that all call requests are
routed to the VCS Control and it only forwards requests back that it can authenticate.
Infrastructure devices
You are recommended to configure your VCS so that infrastructure products, such as MCUs, register to a
dedicated subzone with an authentication policy set to
Treat as authenticated
.
Configuring VCS authentication methods
The VCS supports 3 different methods of verifying authentication credentials:
n
against an on-box
local database
(which includes any Cisco TMS-supplied credentials)
n
via an LDAP connection to an external
H.350 directory service
n
via direct access to an
Active Directory server
using a Kerberos connection (NTLM challenges only)
The VCS attempts to verify the credentials presented to it by first checking against its on-box local database
of usernames and passwords. The local database also includes checking against credentials supplied by
Cisco TMS if your system is using device provisioning. If the username is not found in the local database, the
VCS may then attempt to verify the credentials via a real-time LDAP connection to an external H.350
Cisco VCS Administrator Guide (X8.1.1)
Page 116 of 507
Device authentication
About device authentication