directory service. The directory service, if configured, must have an H.350 directory schema for either a
Microsoft Active Directory LDAP server or an OpenLDAP server.
Along with one of the above methods, for those devices that support NTLM challenges, the VCS can
alternatively verify credentials via direct access to an Active Directory server using a Kerberos connection.
The direct Active Directory authentication via Kerberos method is only supported by a limited range of
endpoints – at the time of writing, only Cisco Jabber for iPad and Jabber Video. If used, other non-supported
endpoint devices will continue to authenticate using one of the other two authentication methods.
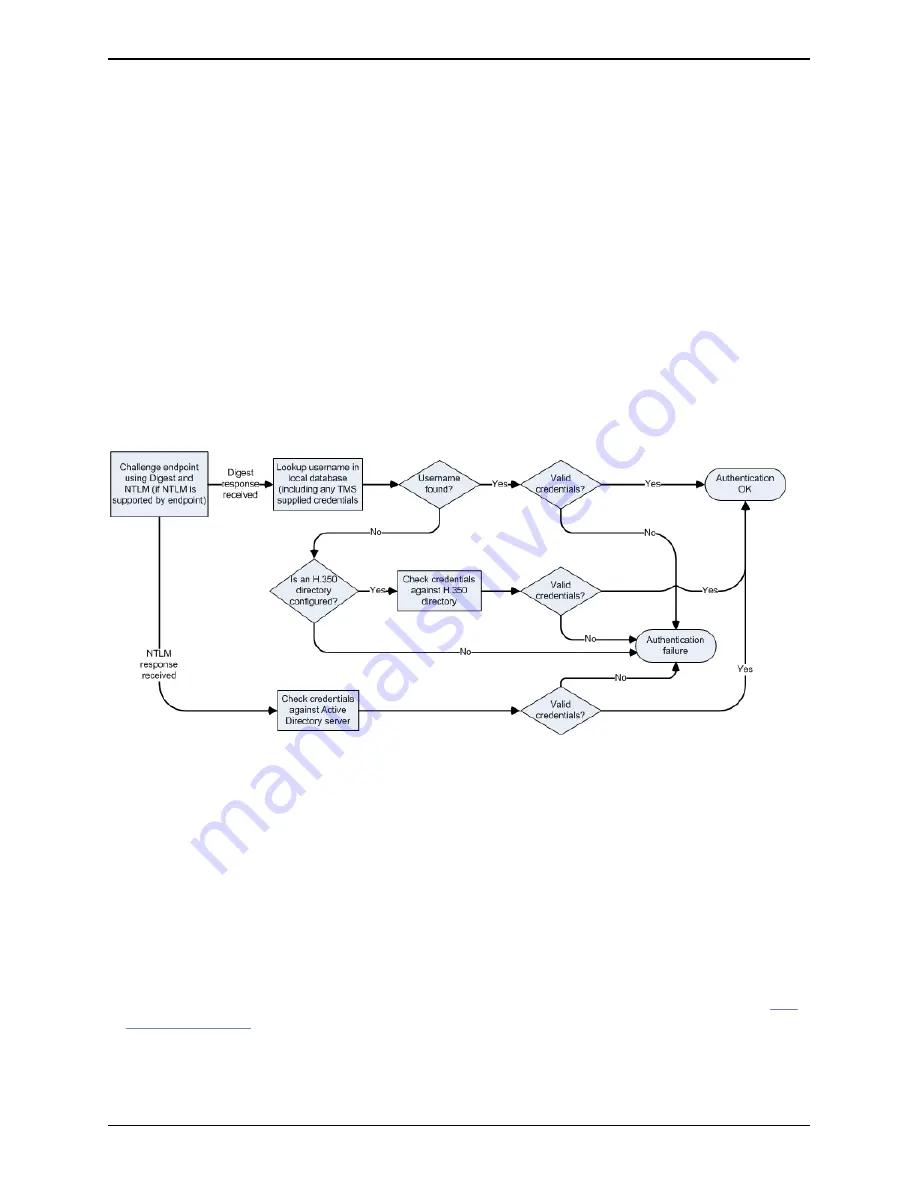
Note that the VCS always challenges an endpoint with a standard Digest challenge. The VCS will
additionally send an NTLM challenge if the VCS has NTLM protocol challenges enabled and it recognizes
that the endpoint supports NTLM.
If the endpoint receives both challenges, it is the endpoint's decision as to whether to respond to the Digest
challenge or to the NTLM challenge. At the time of writing, all supported endpoints respond to an NTLM
challenge in preference to a Digest challenge.
The following diagram shows the process followed by the VCS when authenticating credentials:
Note that accurate timestamps play an important part in authentication of H.323 devices, helping to guard
against replay attacks. For this reason, if you are using device authentication with H.323 devices, both the
VCS and the endpoints must use an NTP server to synchronize their system time.
Authentication mechanism
The authentication process uses a username and password-based challenge-response scheme to check a
device's credentials.
The actual mechanism used by the device to supply its credentials to the VCS depends on the protocol being
used:
n
H.323
: any necessary credentials are contained within the incoming request. (The VCS supports the
ITU
H.235 specification
for authenticating the identity of H.323 network devices with which it communicates.)
n
SIP
: credentials are not contained within the initial request. Instead the VCS sends a challenge back to the
sender that asks for its credentials. However, if a SIP message has already been authenticated (for
Cisco VCS Administrator Guide (X8.1.1)
Page 117 of 507
Device authentication
About device authentication