Configuring the LDAP server settings
1. Go to
Configuration > Authentication > Devices > H.350 directory service
.
2. Configure the fields as follows:
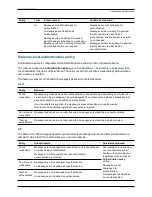
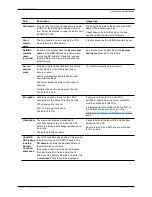
Field
Description
Usage tips
H.350 device
authentication
Enables or disables the use of an H.350
directory for device authentication.
The H.350 directory can be used in
combination with other authentication
mechanisms.
Source of
aliases for
registration
Determines how aliases are checked and
registered.
See
H.350 directory authentication and
registration process
above for a
description of each setting.
When
Source of aliases for registration
is
H.350 directory
, MCUs are treated as a
special case. They register with the
presented aliases and ignore any aliases in
the H.350 directory. (This is to allow MCUs
to additively register aliases for
conferences.)
Server
address
The IP address or FQDN (or server address,
if a DNS
Domain name
has also been
configured) of the LDAP server.
The LDAP server must have the H.350
schemas installed.
FQDN
address
resolution
Defines how the LDAP
Server address
is
resolved if it is specified as an FQDN.
Address record
: DNS A or AAAA record
lookup.
SRV record
: DNS SRV record lookup.
The default is
Address record
.
DNS SRV lookups enable the VCS to
authenticate devices against multiple
remote H.350 directory servers. This
provides a seamless redundancy
mechanism in the event of reachability
problems to an H.350 directory server.
The SRV lookup is for either _ldap._tcp or _
ldap._tls records, depending on whether
Encryption
is enabled. If multiple servers
are returned, the priority and weight of each
SRV record determines the order in which
the servers are used.
Port
The IP port of the LDAP server.
Typically, non-secure connections use
389
and secure connections use
636
.
Encryption
Determines whether the connection to the
LDAP server is encrypted using Transport
Layer Security (TLS).
TLS
: uses TLS encryption for the connection
to the LDAP server.
Off
: no encryption is used.
The default is
TLS
.
When TLS is enabled, the LDAP server’s
certificate must be signed by an authority
within the VCS’s trusted CA certificates file.
Click
Upload a CA certificate file for TLS
(in the
Related tasks
section) to go to the
Managing the trusted CA certificate list
[p.285]
page.
Bind DN
The user distinguished name used by the
VCS when binding to the LDAP server.
For example, uid=admin, ou=system
Bind
password
The password used by the VCS when binding
to the LDAP server.
Cisco VCS Administrator Guide (X8.1.1)
Page 121 of 507
Device authentication
About device authentication