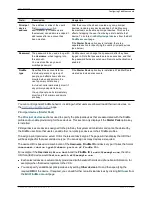
Error message
Reason / resolution
Invalid server name or DNS failure
DNS resolution of the LDAP server name is failing.
Invalid bind credentials
Check
Bind DN
and
Bind password
, this error can also be displayed if
SASL is set to
DIGEST-MD5
when it should be set to
None
.
Invalid bind DN
Check
Bind DN
; the current value does not describe a valid account in
the LDAP director.
This failed state may be wrongly reported if the
Bind DN
is 74 or more
characters in length. To check whether there is a real failure or not, set
up an administrator group on the VCS using a valid group name. If
VCS reports “saved” then there is not a problem (the VCS checks that
it can find the group specified). If it reports that the group cannot be
found then either the
Bind DN
is wrong, the group is wrong or one of
the other configuration items may be wrong.
There is no CA certificate installed
CA certificate, private key and server certificate are required for TLS.
Unable to get configuration
LDAP server information may be missing or incorrect.
Configuring administrator groups
The
Administrator groups
page (
Users > Administrator groups
) lists all the administrator groups that
have been configured on the VCS, and lets you add, edit and delete groups.
Administrator groups only apply if
remote account authentication
is enabled.
When an administrator logs in to the VCS web interface, their credentials are authenticated against the
remote directory service and they are assigned the access rights associated with the group to which the
administrator belongs. If the administrator account belongs to more than one group, the highest level
permission is assigned.
The configurable options are:
Field
Description
Usage tips
Name
The name of the administrator group.
It cannot contain any of the following characters:
/ \ [ ] : ; | = , + * ? > < @ "
The group names defined in the VCS must
match the group names that have been set up
in the remote directory service to manage
administrator access to this VCS.
Cisco VCS Administrator Guide (X8.1.1)
Page 268 of 507
User accounts
Configuring remote account authentication using LDAP