ID
Title
Description
Solution
Severity
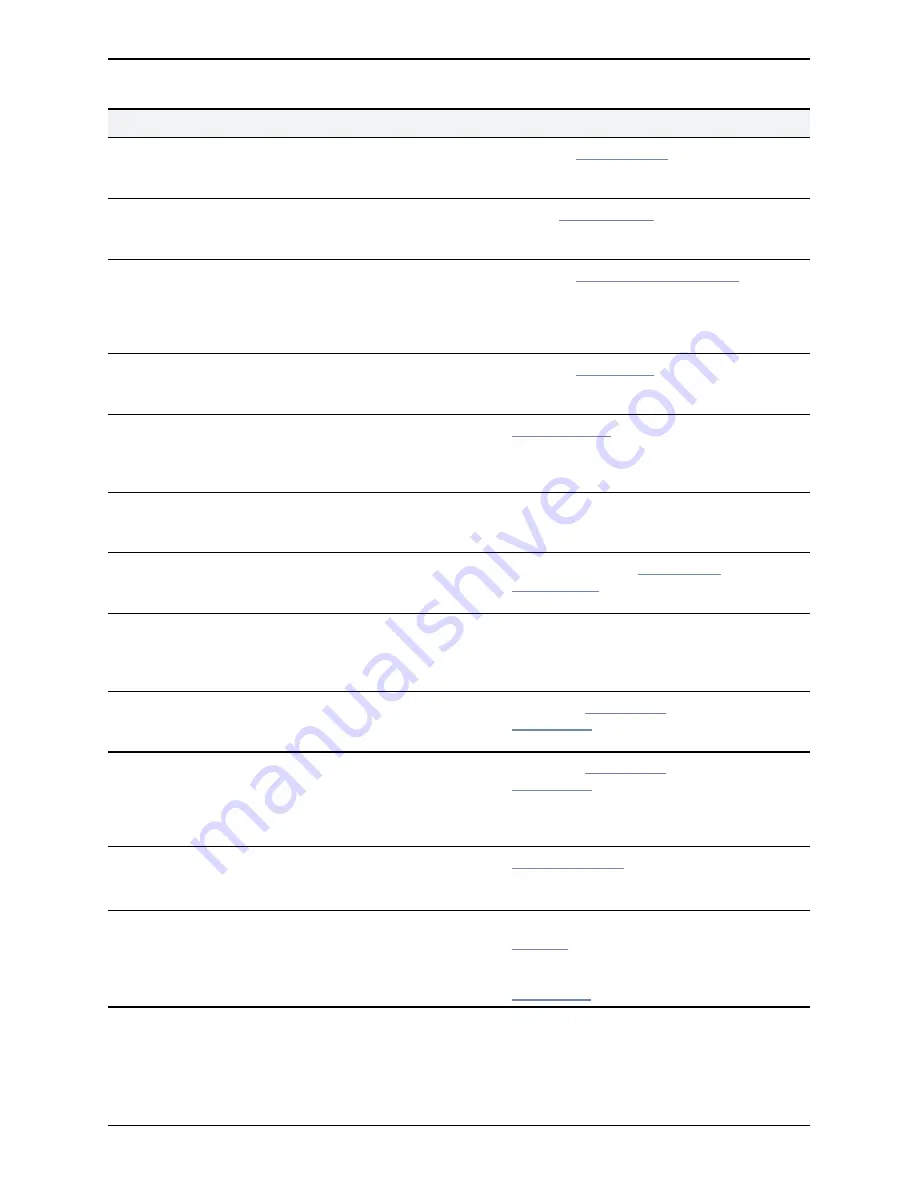
40021 Remote logging
enabled
You are recommended to disable
the remote syslog server when in
advanced account security mode
Configure
remote logging
Warning
40022 Security alert
Active Directory secure channel
disabled; you are recommended to
enable the secure channel setting
Enable
secure channel
Warning
40024 CRL checking
required
Your login account LDAP server
configuration is recommended to
have certificate revocation list (CRL)
checking set to
All
when in
advanced account security mode
Configure
login account LDAP server
Warning
40025 SNMP enabled
You are recommended to disable
SNMP when in advanced account
security mode
Configure
SNMP mode
Warning
40026 Reboot required
The advanced account security
mode has changed, however a
reboot is required for this to take
effect
Reboot the VCS
Warning
40027 Security alert
The connection to the TMS
Provisioning Extension services is
not using TLS encryption
Configure TMS Provisioning
Extension services connection
settings
Warning
40028 Insecure
password in use
The root user's password is hashed
using MD5, which is not secure
enough
View instructions on
changing the
root password
Warning
40029 LDAP server CA
certificate is
missing
A valid CA certificate for the LDAP
database has not been uploaded;
this is required for connections via
TLS
Upload a valid CA certificate
Warning
40030 Security alert
Firewall rules activation failed; the
firewall configuration contains at
least one rejected rule
Check your
firewall rules
configuration
, fix any rejected rules
and re-try the activation
Warning
40031 Security alert
Unable to restore previous firewall
configuration
Check your
firewall rules
configuration
, fix any rejected rules,
activate and accept the rules; if the
problem persists, contact your Cisco
representative
Warning
40032 Security alert
Unable to initialize firewall
Restart the system
; if the problem
persists, contact your Cisco
representative
Warning
40033 Configuration
warning
The Default Zone access rules are
enabled, but leaving SIP over UDP
or SIP over TCP enabled offers a
way to circumvent this security
feature
Either disable UDP and TCP on the
SIP page
to enforce certificate
identity checking using TLS, or
disable the access rules for the
Default Zone
.
Warning
Cisco VCS Administrator Guide (X8.1.1)
Page 414 of 507
Reference material
Alarms