23
Chapter 6: Using the WLAN Monitor
Creating a New Profile
Wireless-G Notebook Adapter
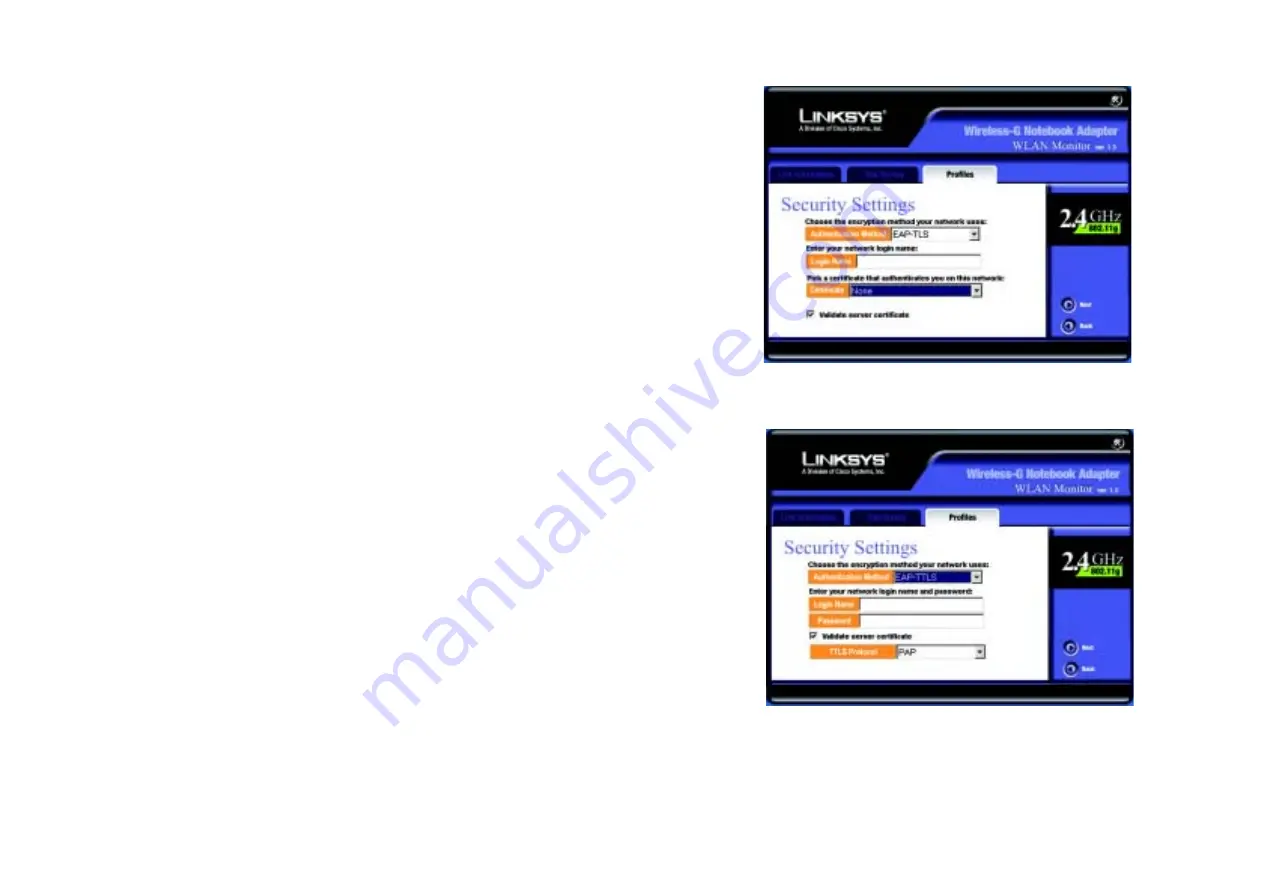
The screen in Figure 6-20 appears next. Select the
Authentication Method
from the drop-down menu. The
options are described below.
EAP-TLS
Enter the Login name of your wireless network in the
Login Name
field. From the
Certificate
drop-down
menu, select the certificate you have installed to authenticate you on your wireless network. Select
Validate server cerificate
to make sure that the certificate for the server is valid.
Click the
Next
button to continue. Click the
Back
button to return to the previous screen.
EAP-TTLS
Enter the Login name of your wireless network in the
Login Name
field. Enter the password of your wireless
network in the
Password
field. Select
Validate server cerificate
to make sure that the certificate for the
server is valid. Select the
TTLS Protocol
from the drop-down menu.
Click the
Next
button to continue. Click the
Back
button to return to the previous screen.
Figure 6-20: EAP-TLS Authentication
Figure 6-21: EAP-TTLS Authentication
















































