Chapter 2 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - How it works - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Chapter 2
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 42 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
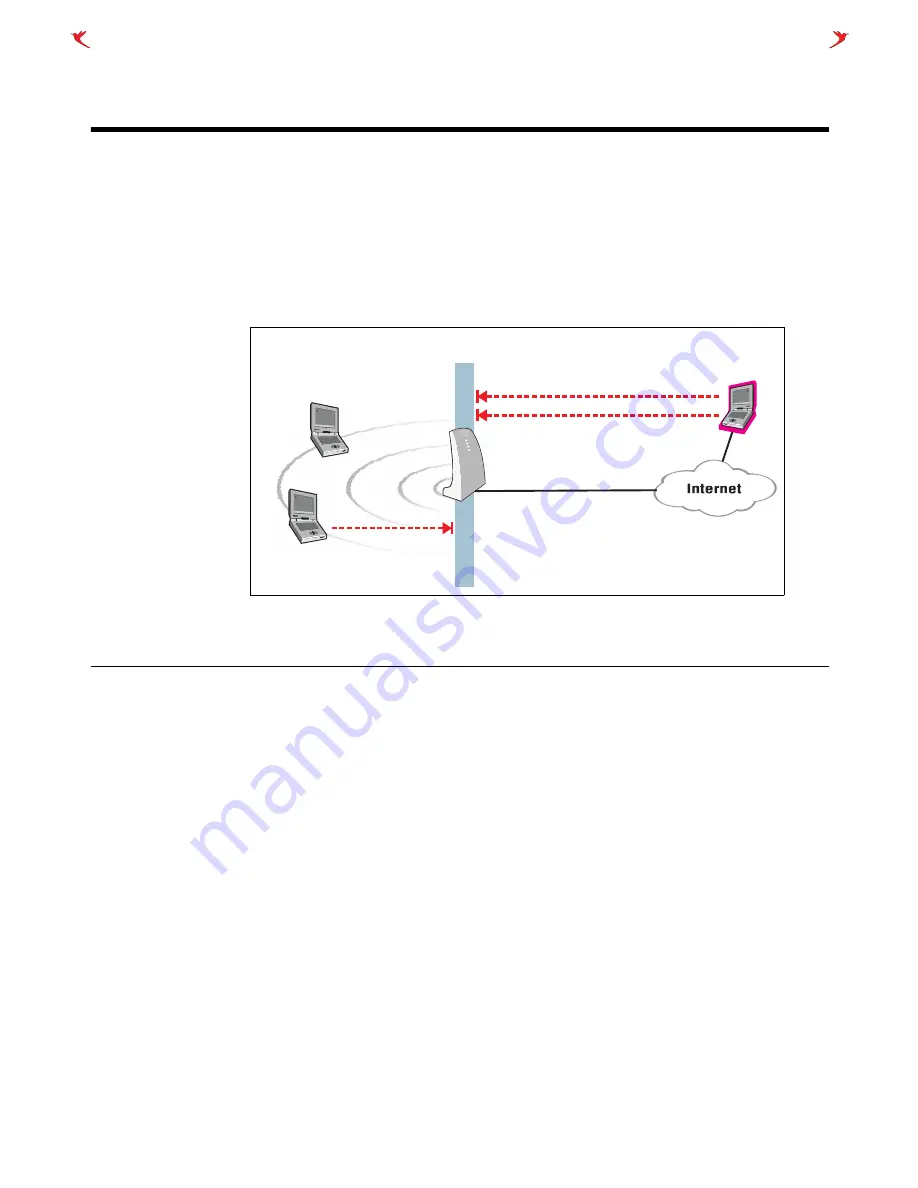
Firewall
To safeguard your network from intruders, the CN3000 features a customizable stateful
firewall. The firewall operates on the traffic streaming through the Internet port. It can be
used to control both incoming and outgoing data.
The CN3000 features a number of predefined firewall rules to let you achieve the
required security level you need without going to the trouble of designing your own
rules. However, if necessary, you can create a completely custom set of firewall rules to
suite your particular networking requirements.
If the CN3000 is connected to a wired LAN, the firewall protects the wired LAN as well.
Blocking unauthorized access with the firewall.
Firewall presets
The easiest way to make use of the firewall is to use one of the preset settings. Three
levels of security are provided:
•
High:
Permits all outgoing traffic, except NetBIOS (TCP and UDP). Blocks all
externally initiated connections.
•
Medium:
Same as High except that it permits incoming PPTP and IPSec
connections.
•
Low:
Permits all incoming and outgoing traffic, except for NetBIOS traffic. Use this
option if you require active FTP sessions.
The following tables indicate how some common applications are affected by the preset
firewall settings.
syn attack
telnet
Integrated
Firewall
ftp
Hacker
Summary of Contents for CN3000
Page 1: ...CN3000 Administrator s Guide...
Page 8: ...Table of Contents 8...
Page 60: ...Chapter 2 How it works Chapter 2 60...
Page 94: ...Chapter 4 Scenarios Chapter 4 94...
Page 106: ...Chapter 5 Activating the public access interface Chapter 5 106...
Page 211: ...Chapter 10 SSL certificates Chapter 10 211...
Page 292: ...Chapter 13 The configuration file Chapter 13 292...
Page 370: ...Chapter 16 Sample setup Microsoft RADIUS Chapter 16 370...
Page 396: ...Chapter 16 Sample setup Microsoft RADIUS Chapter 16 396...
Page 414: ...Chapter 17 Experimenting with NOC authentication Chapter 17 414...
















































