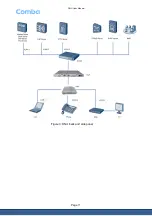
ONU User Manual
Page 6
Figure 64: IPSec Tunnel Model Conntctions window .......................................................................... 69
Figure 65: IPSec Settings window ....................................................................................................... 70
Figure 66: Wireless--Bridge window .................................................................................................... 72
Figure 67: Wireless--Advanced window .............................................................................................. 73
Figure 68: Wireless--
Authenticated Stations ...................................................................................... 76
Figure 69: Voice—SIP Basic Setting window ...................................................................................... 77
Figure 70: Voice—SIP configuration window ....................................................................................... 78
Figure 71: Voice—SIP Advanced setting window ................................................................................ 80
Figure 72: Voice—SIP Advanced configuration window ...................................................................... 81
Figure 73: Voice—SIP Debug setting window ..................................................................................... 84
Figure 74: Voice—SIP Debug configuration window ........................................................................... 84
Figure 75: Diagnostics window ............................................................................................................ 85
Figure 76: Backup window ................................................................................................................... 86
Figure 77: Update Settings window ..................................................................................................... 87
Figure 78: Restore Default Settings window ........................................................................................ 87
Figure 79: System Log window ............................................................................................................ 88
Figure 80: System Log information window ......................................................................................... 88
Figure 81: Configuration window ......................................................................................................... 89
Figure 82: Security Log window ........................................................................................................... 90
Figure 83: Security Log information window ........................................................................................ 91