130
Appendix A - Firewall
STATEFUL PACKET INSPECTION
Refers to an architecture, where the firewall keeps track of packets on each
connection traversing all its interfaces and makes sure they are valid. This is in
contrast to static packet filtering which only examines a packet based on the
information in the packet header.
DENIAL OF SERVICE ATTACK
Is an incident in which a user or organization is deprived of the services of a
resource they would normally expect to have. Various DoS attacks the device can
withstand are ARP Attack, Ping Attack, Ping of Death, Land, SYN Attack, Smurf
Attack, and Tear Drop.
TCP/IP/PORT/INTERFACE FILTER
These rules help in the filtering of traffic at the Network layer (i.e. Layer 3).
When a Routing interface is created,
Enable Firewall
must be checked.
Navigate to Advanced Setup
Security
IP Filtering.
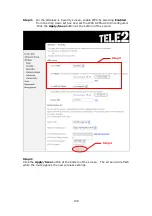
OUTGOING IP FILTER
Helps in setting rules to DROP packets from the LAN interface. By default, if the
Firewall is Enabled, all IP traffic from the LAN is allowed. By setting up one or more
filters, specific packet types coming from the LAN can be dropped.
Example 1:
Filter Name
: Out_Filter1
Protocol
: TCP
Source IP address
: 192.168.1.45
Source Subnet Mask
: 255.255.255.0
Source Port
: 80
Dest. IP Address
: NA
Dest. Subnet Mask
: NA
Dest. Port
: NA
This filter will Drop all TCP packets coming from the LAN with IP
Address/Subnet Mask of 192.168.1.45/24 having a source port of 80
irrespective of the destination. All other packets will be Accepted.
Example 2:
Filter Name
: Out_Filter2
Protocol
: UDP
Source IP Address
: 192.168.1.45
Source Subnet Mask
: 255.255.255.0
Source Port
: 5060:6060
Dest. IP Address
: 172.16.13.4
Dest. Subnet Mask
: 255.255.255.0
Dest. Port
: 6060:7070
This filter will drop all UDP packets coming from the LAN with IP Address /
Subnet Mask of 192.168.1.45/24 and a source port range of 5060 to 6060,
destined to 172.16.13.4/24 and a destination port range of 6060 to 7070.
INCOMING IP FILTER
Helps in setting rules to Allow or Deny packets from the WAN interface. By default,
all incoming IP traffic from the WAN is Blocked, if the Firewall is Enabled. By setting
up one or more filters, specific packet types coming from the WAN can be Accepted.
Summary of Contents for VI-3223u
Page 1: ...VI 3223u Multi DSL WLAN IAD User Manual Version B1 0 July 19 2013 261099 020...
Page 7: ...6 1 2 Application The following diagram depicts a typical application of the VI 3223u...
Page 16: ...15 STEP 3 After successfully logging in for the first time you will reach this screen...
Page 26: ...25...
Page 32: ...31 Chapter 5 Advanced Setup The following screen shows the advanced menu options...
Page 67: ...66 5 11 UPnP Select the checkbox provided and click Apply Save to enable UPnP protocol...
Page 72: ...71 5 15 1 Storage Device Info Display after storage device attached for your reference...
Page 74: ...73 Automatically Add Clients With Following DHCP Vendor IDs...
Page 98: ...97 Click Apply Save to set new advanced wireless options...
Page 103: ...102 7 1 SIP Basic Setting 7 1 1 Global Parameters A common parameter setting...
Page 104: ...103 7 1 2 Service Provider This screen contains basic SIP configuration settings...
Page 106: ...105 7 2 SIP Advanced This screen contains the advanced SIP configuration settings...
Page 107: ...106 7 2 1 Global Parameters A common parameter setting...
Page 172: ...171 Click Next to continue or click Back to return to the previous step...