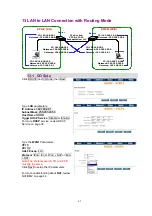
65
14 Configuration via Serial Console or Telnet with Menu
Driven Interface
14.1 Serial
Console
Check the connectivity of the RS-232 cable from your computer to the serial port of ROUTER. Start your
terminal access program by VT100 terminal emulation with the following parameters:
Parameter Value
Baudrate
9600
Data Bits
8
Parity Check
No
Stop Bits
1
Flow-control No
Press the SPACE key until the login screen appears. When you see the login screen, you can logon to
Router.
Note: Only SPACE key invoke the login prompt. Pressing other keys does not work.
User: admin
Password: *****
Note: The factory default
User
and
Password
are “admin” both.
14.2 Telnet
Make sure the correct Ethernet cable connected the LAN port of your computer to ROUTER. The LAN
LNK indicator on the front panel shall light if a correct cable is used. Starting your Telnet client with
VT100 terminal emulation and connecting to the management IP of Router, wait for the login prompt
appears. Input User and Password after login screen pop up,
User: admin
Password: *****
Note: The default IP address is 192.168.0.1.
14.3 Operation Interface
For serial console and Telnet management, the ROUTER implements two operational interfaces:
Command Line Interface (CLI) and menu driven interface. The CLI mode provides users a simple
interface, which is better for working with script file. The menu driven interface is a user-friendly
interface to general operations. The command syntax for CLI is the same as that of the menu driven
interface. The only difference is that the menu driven interface shows you all of available commands for
you to select. You don’t need to remember the command syntax and save your time on typing the
whole command line.
The following figure gives you an example of the menu driven interface. In the menu, you scroll
up/down by pressing key I / K, select one command by key L, and go back to a higher level of menu by
key J. For example, to show the system information, just logon to the ROUTER, move down the cursor
by pressing key K twice and select “show” command by key L, you shall see a submenu and select
“system” command in this submenu, then the system will show you the general information.
Summary of Contents for SHDTU03b
Page 1: ...USER MANUAL SHDTU03b G SHDSL bis Bridge Router Modems CTC Union Technologies Co Ltd ...
Page 2: ......
Page 8: ......
Page 95: ......