DES-3028 DES-3028P DES-3028G DES-3052 DES-3052P Layer 2 Fast Ethernet Managed Switch
This protocol will also tag BPDU packets so receiving devices can distinguish spanning tree instances, spanning tree regions and
the VLANs associated with them. An MSTI ID will classify these instances. MSTP will connect multiple spanning trees with a
Common and Internal Spanning Tree (CIST). The CIST will automatically determine each MSTP region, its maximum possible
extent and will appear as one virtual bridge that runs a single spanning tree. Consequentially, frames assigned to different VLANs
will follow different data routes within administratively established regions on the network, continuing to allow simple and full
processing of frames, regardless of administrative errors in defining VLANs and their respective spanning trees.
Each switch utilizing the MSTP on a network will have a single MSTP configuration that will have the following three attributes:
1.
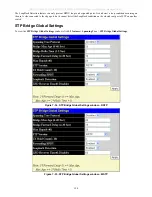
A configuration name defined by an alphanumeric string of up to 32 characters (defined in the
STP Bridge Global
Settings
window in the Configuration Name
field).
2.
A configuration revision number (named here as a Revision Level and found in the
STP Bridge Global Settings
window)
and;
3.
A 4096-element table (defined here as a VID List in the
MST Configuration Table
window), which will associate each
of the possible 4096, VLANs supported by the Switch for a given instance.
To utilize the MSTP function on the Switch, three steps need to be taken:
1.
The Switch must be set to the MSTP setting (found in the
STP Bridge Global Settings
window in the STP Version field)
2.
The correct spanning tree priority for the MSTP instance must be entered (defined here as a Priority in the
MST
Configuration Table
window when configuring an MSTI ID
settings).
3.
VLANs that will be shared must be added to the MSTP Instance ID (defined here as a
VID List
in the
MST
Configuration
Table
window when configuring an MSTI ID settings).
802.1w Rapid Spanning Tree
The Switch implements two versions of the Spanning Tree Protocol, the Rapid Spanning Tree Protocol (RSTP) as defined by the
IEEE 802.1w specification and a version compatible with the IEEE 802.1d STP. RSTP can operate with legacy equipment
implementing IEEE 802.1d, however the advantages of using RSTP will be lost.
The IEEE 802.1w Rapid Spanning Tree Protocol (RSTP) evolved from the 802.1d STP standard. RSTP was developed in order to
overcome some limitations of STP that impede the function of some recent switching innovations, in particular, certain Layer 3
functions that are increasingly handled by Ethernet switches. The basic function and much of the terminology is the same as STP.
Most of the settings configured for STP are also used for RSTP. This section introduces some new Spanning Tree concepts and
illustrates the main differences between the two protocols.
Port Transition States
An essential difference between the three protocols is in the way ports transition to a forwarding state and in the way this
transition relates to the role of the port (forwarding or not forwarding) in the topology. RSTP combines the transition states
disabled, blocking and listening used in 802.1d and creates a single state Discarding. In either case, ports do not forward packets.
In the STP port transition states disabled, blocking or listening or in the RSTP port state discarding, there is no functional
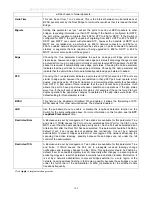
difference, the port is not active in the network topology. Table 6-2 below compares how the two protocols differ regarding the
port state transition.
All three protocols calculate a stable topology in the same way. Every segment will have a single path to the root bridge. All
bridges listen for BPDU packets. However, BPDU packets are sent more frequently - with every Hello packet. BPDU packets are
sent even if a BPDU packet was not received. Therefore, each link between bridges is sensitive to the status of the link. Ultimately
this difference results in faster detection of failed links, and thus faster topology adjustment. A drawback of 802.1d is this absence
of immediate feedback from adjacent bridges.
802.1w RSTP
802.1d STP
Forwarding
Learning
Discarding Disabled No
No
Discarding Blocking No
No
Discarding Listening No
No
Learning Learning No
Yes
Forwarding Forwarding Yes
Yes
Table 7- 2. Comparing Port States
118
Summary of Contents for DES-3028
Page 306: ......
Page 307: ......
Page 327: ...D Link D Link D Link D Link 7 495 744 00 99 http www dlink ru e mail support dlink ru...
Page 332: ...Technical Support Web Web URL http www dlink jp com...