xStack
®
DES-3528/DES-3552 Series Layer 2 Stackable Fast Ethernet Managed Switch User Manual
185
Port-Based Network Access Control
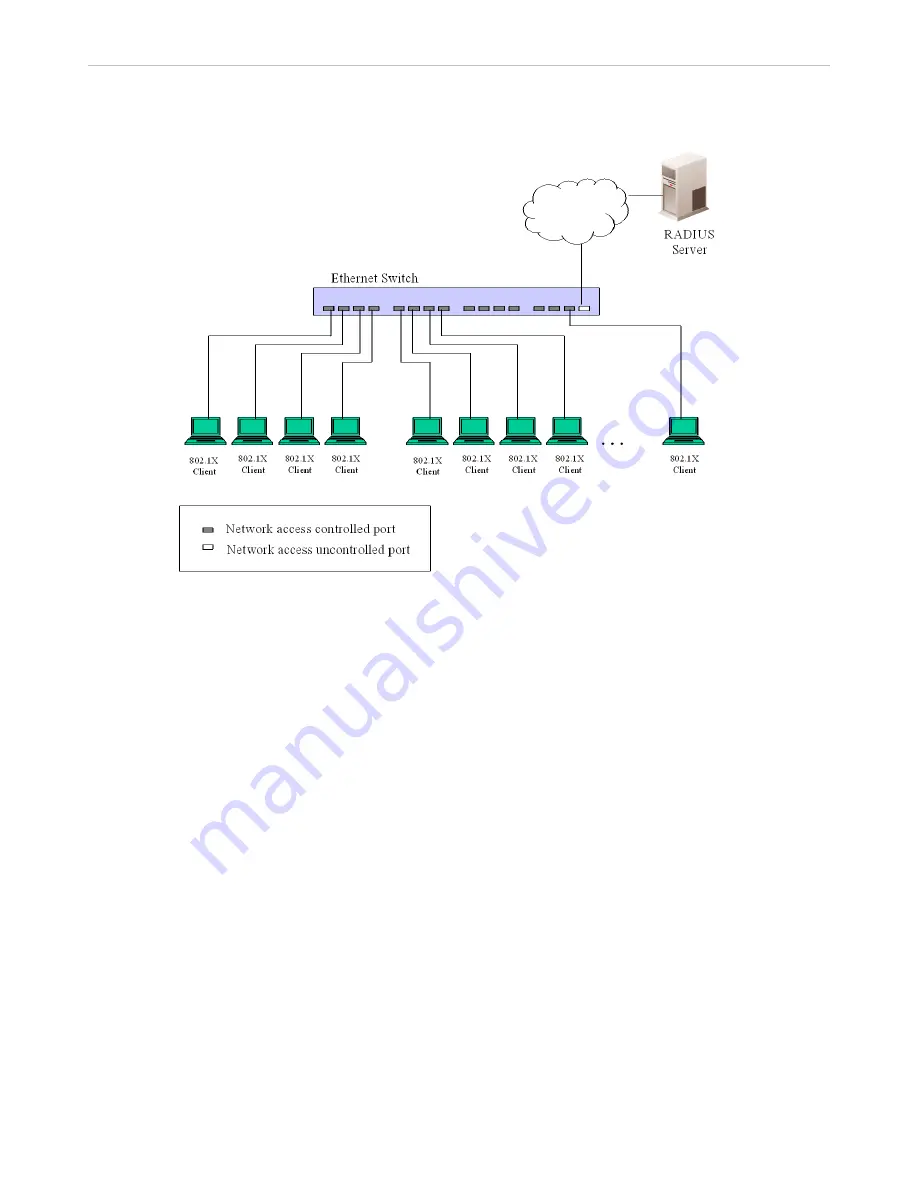
Figure 6 - 19 Example of Typical Port-Based Configuration
Once the connected device has been successfully authenticated, the Port then becomes Authorized, and all
subsequent traffic on the Port is not subject to access control restriction until an event occurs that causes the Port to
become Unauthorized. Hence, if there are more than one device connecting to a port (for example, these devices go
through a switch to access this port), and once one of the devices passes authenticating, then all other devices that is
connected to this port can access this port. Clearly, the security offered in this situation is open to attack.
Summary of Contents for DES-3528 - xStack Switch - Stackable
Page 19: ...xStack DES 3528 DES 3552 Series Layer 2 Stackable Fast Ethernet Managed Switch User Manual 18...
Page 214: ...xStack DES 3528 DES 3552 Series Layer 2 Stackable Fast Ethernet Managed Switch User Manual 213...
Page 306: ...xStack DES 3528 DES 3552 Series Layer 2 Stackable Fast Ethernet Managed Switch User Manual 305...