Network Address Translation (NAT)
In NAT mode, the DFL-1000 is installed as a privacy barrier between the internal network and the Internet.
The firewall provides network address translation to protect the private network. In NAT mode, you can
add a DMZ network to provide public access to Internal servers while protecting them behind the firewall
on a separate internal network.
Features supported in NAT mode include:
•
Firewall protection, allow/deny traffic according to source/destination address, service, and time of
day
•
VPN, virus protection, and Web content filtering
•
IP/MAC binding
•
DHCP configuration of the DFL-1000 external network address
•
Detailed logging
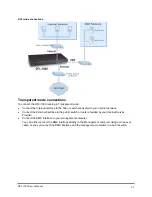
Transparent mode
Transparent Mode provides even quicker and easier installation when the requirement is to provide
firewall protection to a pre-existing network with public addresses. The internal and external network
interfaces of the DFL-1000 can be in the same network; therefore, the DFL-1000 can be inserted into
your network at any point without the need to make any changes to your network.
Packets arriving at the DFL-1000 are intelligently forwarded to the correct network interface and firewall
policies prevent unauthorized access to your network.
Transparent mode provides the same basic firewall protection as NAT mode. However, more advanced
features such as the DMZ network, VPN, virus scanning, and content filtering are only available in NAT
mode.
Hacker prevention and protection
The DFL-1000 is built to defend your network from network attacks including:
•
Distributed Denial-Of-Service (DDOS) attacks
SYN Attack
ICMP Flood
UDP Flood
•
IP fragmentation attacks
Ping of Death Attack
Tear Drop Attack
Land Attack
•
Port Scan Attack
•
IP Source Routing
•
IP Spoofing Attack
•
Address Sweep Attack
•
WinNuke Attack
You can configure email alerts that send an email to the system administrator when the DFL-1000 detects
one of these attacks. You can also configure email alerts to provide real time warnings of ongoing attacks.
Up to three email recipients can be specified.
DFL-1000 User’s Manual
10