Log Traffic
Optionally select Log Traffic to add messages to the traffic log whenever the policy accepts a
connection.
Traffic
Shaping
Optionally, select Traffic Shaping to control the bandwidth available to and set the priority of
the traffic processed by the policy.
•
Click OK to save the policy.
The deny policy is added to the policy list above the policy that accepts connections.
Example policy to deny access:
Arranging policies in the incoming policy list
Arrange policies in the incoming policy list to make sure that the policies function as you expect them to.
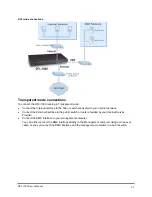
When the DFL-1000 receives a connection attempt from the Internet, it decides whether to accept or deny
the connection by matching it with a policy on the Incoming policy list. The first policy to match the
connection attempt is applied. Because policies are selected on a first match basis, you must arrange
policies in the policy list so that they have the effect that you expect them to. In general, you should
arrange policies that deny connections above policies that accept connections. For more information on
policy matching, see
From the policy list you can re-arrange policies, delete policies, and edit policies. For more information,
see
Arranging policies in the policy list
.
Controlling connections to the Internet
By default, the DFL-1000 accepts all connections from the internal network to the Internet. If you do not
want to enforce restrictions on access to the Internet, you do not have to change anything. The default
policy accepts connections from any address on the internal network to any address on the Internet at
any time, and for any service.
If you want to control connections to the Internet, you have three choices:
•
Add exceptions to the default policy that deny connections
•
Add exceptions to the default policy that require authentication
•
Delete the default policy and then add policies that accept connections
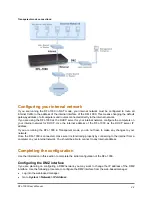
In NAT mode, policies for connections from the internal network to the Internet are added to the Internal
to External (Int to Ext) policies list. In Transparent mode, these policies are added to the Outgoing policies
list.
In NAT mode you can also create policies for connections from the Internal network to the DMZ network.
Policies for these connections are described in
Controlling connections to and from the DMZ
.
This section describes:
•
Denying connections to the Internet from the internal network
•
Accepting connections to the Internet from the internal network
•
Requiring authentication to connect to the Internet
DFL-1000 User’s Manual
29