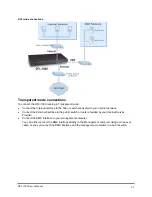
The parts of a DFL-1000 policy
Identifying information
Source
Address
The IP address from which a user or service can connect to the firewall.
Destination
Address
The location to which a user or service is attempting to connect when intercepted by the firewall.
Schedule
The time or date on which a policy is active.
Service
The network service to be provided through the firewall.
Action
Action
The response of the firewall. The firewall can accept the connection, deny the connection, or require
the user attempting to make the connection to provide authentication.
Log Traffic
Log Traffic adds messages to the traffic log whenever the policy processes traffic. For information
about logging, see
Traffic Shaping
Traffic Shaping can be used to control the bandwidth available to, and set the priority of the traffic
processed by the policy. For more information about traffic shaping, see
Default policy
The default policy accepts connections from all computers at any source address on the internal network
and grants them access to any services on the external network (usually the Internet). The default policy
appears in the Int to Ext policy list when running in NAT mode and in the Outgoing policy list when
running in Transparent mode.
shows the default policy.
Default policy:
Adding policies
Policies can be simple to add. For example, you can prevent users on the internal network from
connecting to FTP servers on the Internet by adding an Int to Ext policy that denies connections to the
FTP service as shown in
Sample Int to Ext policy to deny FTP connections
.
Sample Int to Ext policy to deny FTP connections:
To add a policy:
•
Go to
Firewall > Policy
.
•
Click the tab corresponding to the type of policy to add.
•
Click New to add a policy.
You can also click Insert Policy before
on a policy in the list to add the new policy above this one.
•
Configure the policy.
DFL-1000 User’s Manual
34