Polices that require authentication must be added to the policy list above matching policies that do
not, otherwise the policy that does not require authentication is selected first.
Virtual IPs
Running the DFL-1000 in NAT mode hides the actual addresses of the computers on your internal and
DMZ networks from the Internet. To provide Internet access to a server on your DMZ or internal network,
you must make an association between the Internet address of the server and the actual IP address of
the computer on the DMZ or internal network that is running the server. This association is called a Virtual
IP.
Once you have created a Virtual IP, you can add Incoming policies to allow access to the server by
adding the virtual IP to the Destination address of the policy.
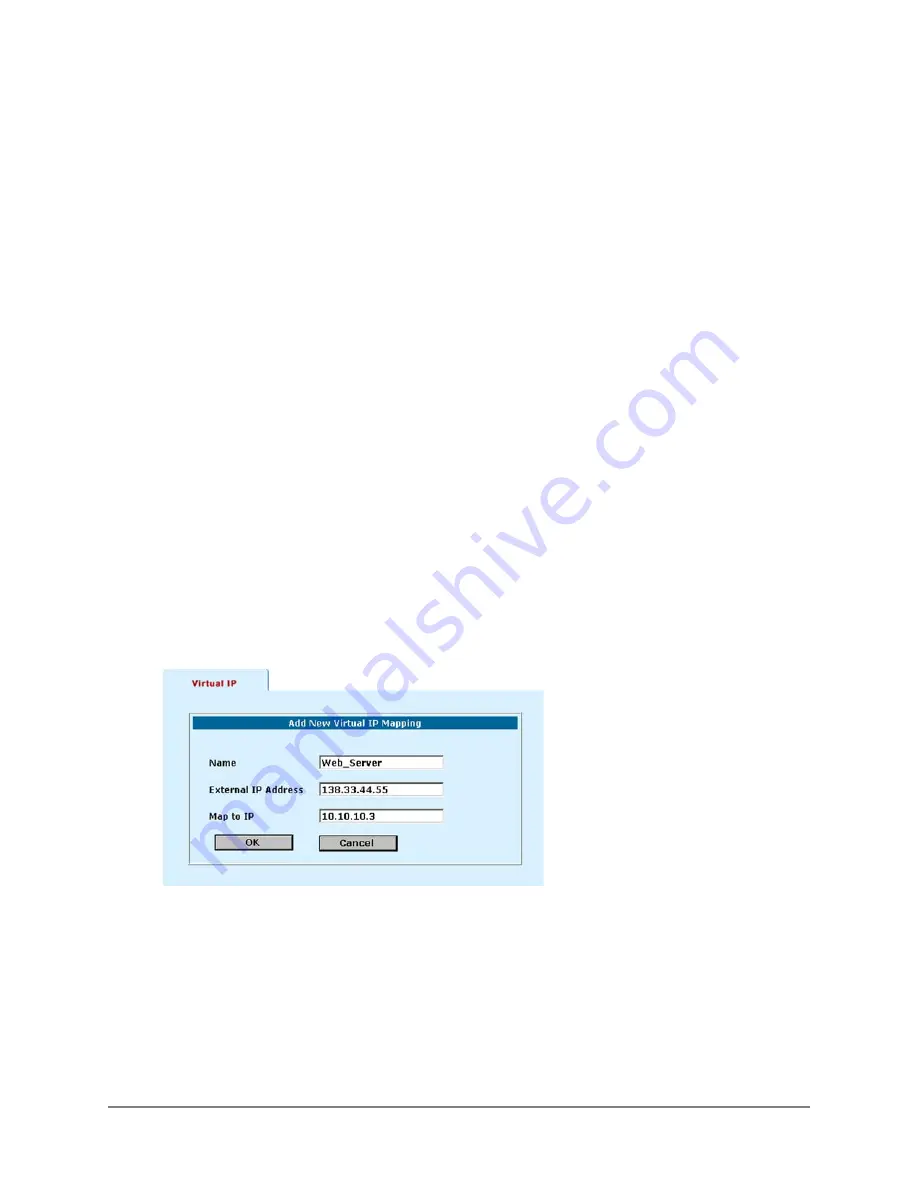
Adding Virtual IPs
To add a Virtual IP:
•
Go to
Firewall > Virtual IP
.
•
Click New to add Virtual IP.
•
Enter a Name for the Virtual IP.
•
In the External IP Address field, enter the Internet IP address of the server.
This must be a static IP address obtained from your ISP for this purpose and must not be the same
as the external address of the DFL-1000. However, your ISP must route this address to the external
IP address of the DFL-1000.
•
In the Map to IP field, enter the actual IP address of the web server on your DMZ or internal network.
•
Click OK to save the Virtual IP.
•
Repeat these steps to add Virtual IPs for all of your internet servers.
Adding a Virtual IP:
IP/MAC binding
IP/MAC binding provides added security against IP Spoofing attacks. IP Spoofing attempts to use the IP
address of a trusted computer to access the DFL-1000 from a different computer. The IP address of a
computer can easily be changed to a trusted address, but MAC addresses are added to ethernet cards at
the factory and cannot easily be changed.
You can enter the IP addresses and corresponding MAC addresses of trusted computers into the DFL-
1000 firewall configuration. When a data packet arrives from a trusted IP address, it is checked to
DFL-1000 User’s Manual
44





































