Example IPSec Autokey VPN Tunnel configuration
Description
Main Office (VPN
Gateway 1)
Branch Office (VPN
Gateway 2)
VPN Tunnel
Name
Use the same name on both ends of the tunnel.
The name can contain alphabetic characters,
numbers and the special characters - and _.
Spaces and the @ character are not allowed.
Branch_Office_VPN Branch_Office_VPN
Remote
Gateway
The External IP address of the VPN gateway at the
other end of the VPN tunnel.
2.2.2.1 1.1.1.1
Keylife
The amount of time (5 to 1440 minutes) before the
encryption key expires. When the key
expires, the VPN gateways generate a new
key without interrupting service.
100 100
Authentication
Key
Enter up to 20 characters. The key must be the
same on both VPN gateways and should
only be known by network administrators.
ddcHH01887d ddcHH01887d
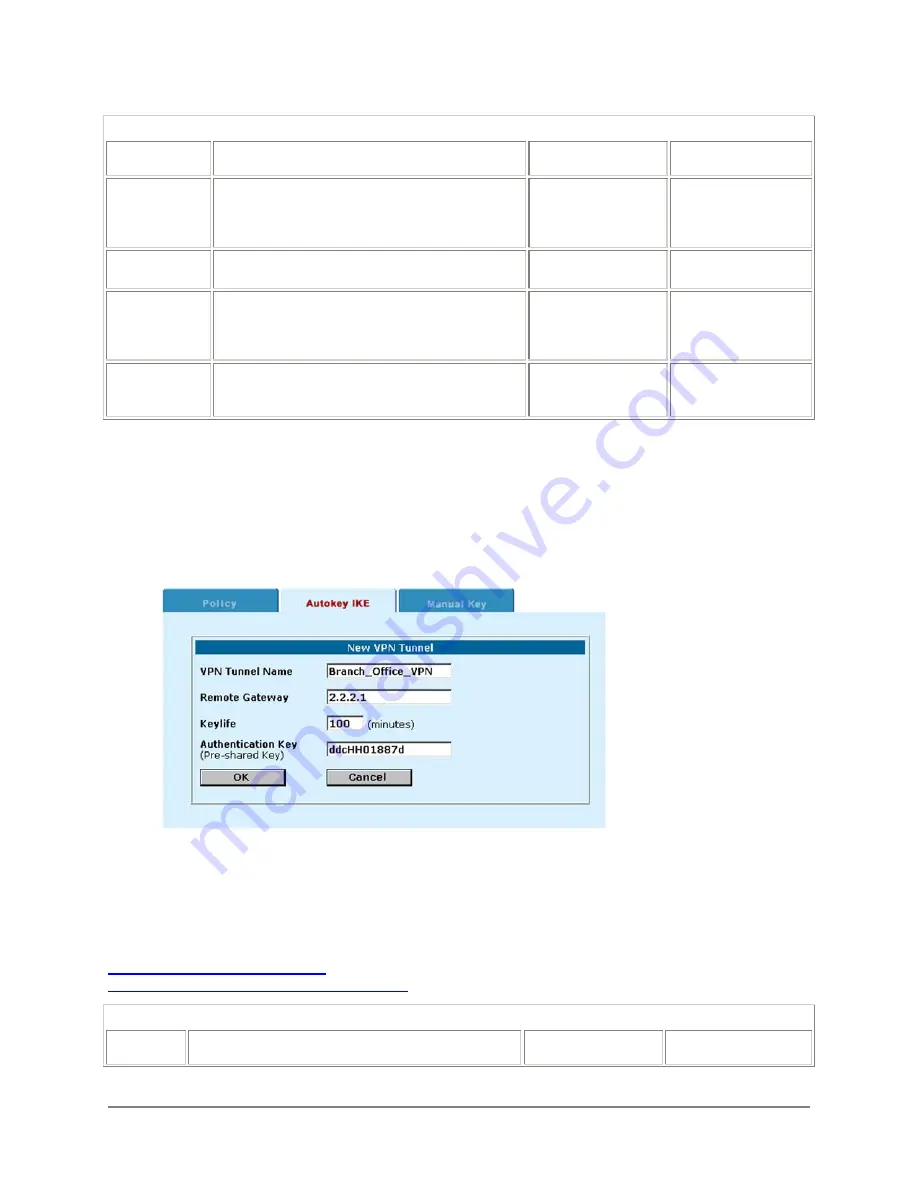
Complete the following procedure on both VPN gateways to configure a VPN tunnel that uses Autokey
IKE key exchange:
•
Go to
VPN > IPSEC > Autokey IKE
.
•
Click New to add a new Autokey IKE VPN tunnel.
•
Enter the VPN Tunnel Name, Remote Gateway, Keylife and Authentication Key.
•
Click OK to save the Autokey IKE VPN tunnel.
Example Main Office Autokey IKE VPN tunnel:
Adding internal and external addresses
The next step in configuring the VPN is to add the addresses of the networks that are to be connected
using the VPN tunnel. On each VPN gateway you must add two addresses:
•
Internal address, the IP address of the network behind the VPN gateway
•
External address, the IP address of the network behind the other VPN gateway
shows the internal and external addresses required for the VPN in
Example VPN between two internal networks
. In the example, both IP addresses are for internal networks.
IPSec Autokey VPN addresses
Description
Main Office (VPN
Gateway 1)
Branch Office (VPN
Gateway 2)
DFL-1000 User’s Manual
49




































