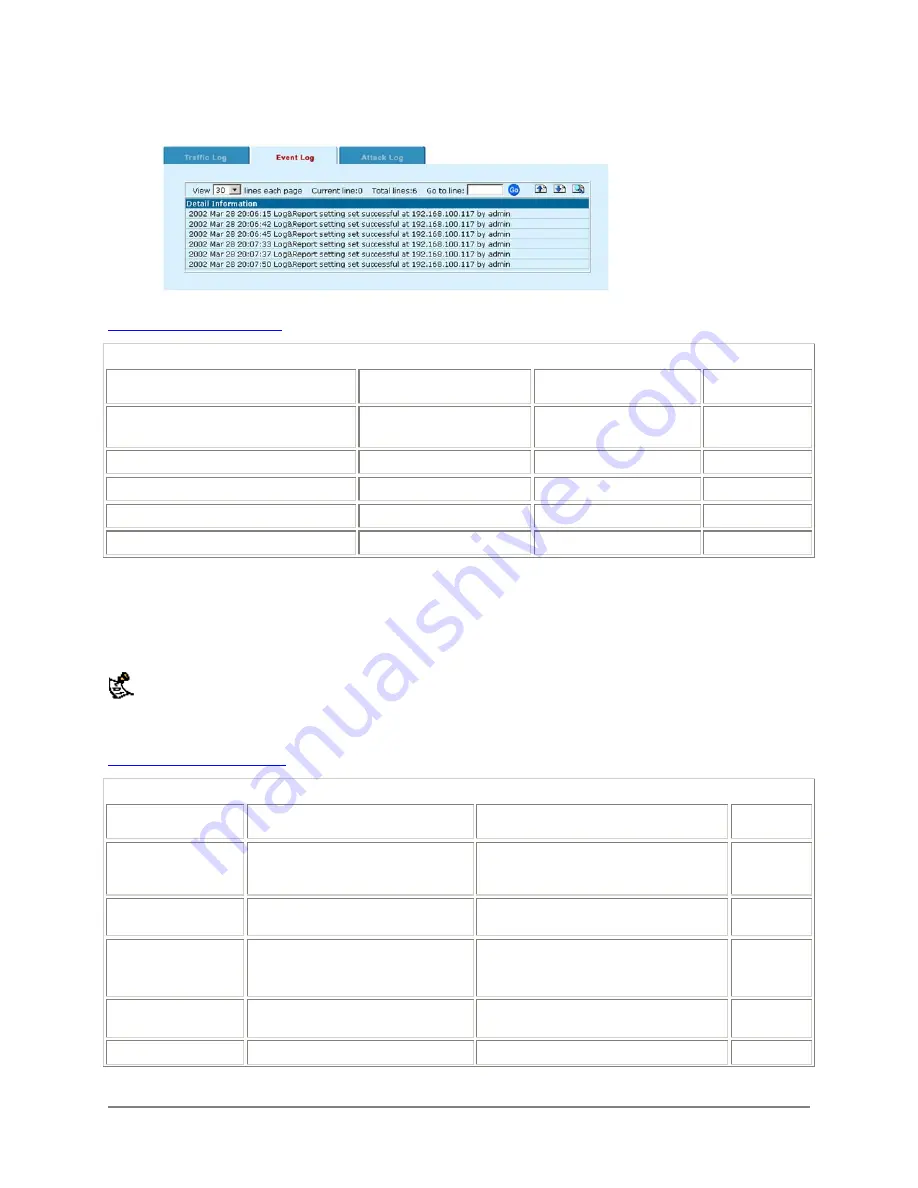
Sample Event Log messages:
describes the event log message format.
Event log message format
Description Format
Example
Maximum
Length
Date and time the log message was
recorded
YYYY MMM DD
hh:mm:ss
2002 Mar 1
15:33:14
15 bytes
Subject or entry number or name
name
httpsd:
12 bytes
Action
action
Network RIP change
10 bytes
Result
successful
or
failed
successful
10 bytes
Host IP address
ipaddress
at 192.168.1.23
15 bytes
Attack log message format
Attack log messages record attacks made on the DFL-1000. Each message records the date and time at
which the attack was made, a description of the attack, and the IP address of the computer from which
the attack originated.
When running in Transparent mode, the DFL-1000 does not create an Attack log.
Attack log messages are created when the DFL-1000 detects one of the attacks listed on the
IDS >
Attack Prevention
page.
describes the attack log message format.
Attack log message format
Description Format
Example
Maximum
Length
Date and time the log
message was
recorded
MMM DD hh:mm:ss
Jan 23 11:11:28
15 bytes
Message describing
type of attack
message
Attack port scan
Start and end times of
attack
between DDD MMM DD
hh:mm:ss YYYY and DDD
MMM DD hh:mm:ss YYYY
between Wed Jan 23 11:06:55
2002 and Wed Jan 23
11:06:28 2002
Source address of the
attack.
from ipaddress
from 23.24.26.78
Destination address
to ipaddress
to 216.21.152.65
DFL-1000 User’s Manual
87