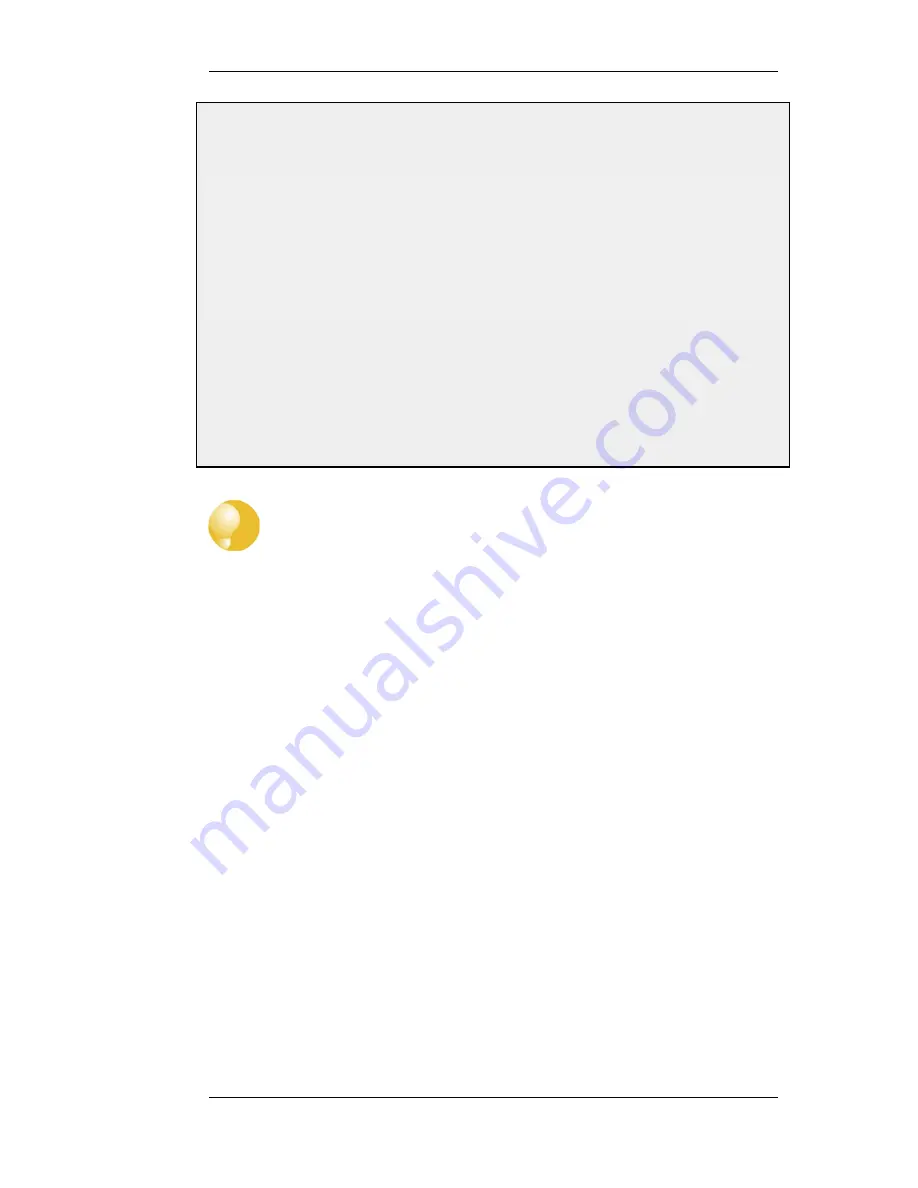
This example illustrates how to display the core routes in the active routing table.
Command-Line Interface
gw-world:/> routes -all
Flags Network
Iface
Gateway
Local IP Metric
----- ------------------ ---------- ------------- -------- ------
127.0.0.1
core
(Shared IP)
0
192.168.0.1
core
(Iface IP)
0
213.124.165.181
core
(Iface IP)
0
127.0.3.1
core
(Iface IP)
0
127.0.4.1
core
(Iface IP)
0
192.168.0.0/24
lan
0
213.124.165.0/24
wan
0
224.0.0.0/4
core
(Iface IP)
0
0.0.0.0/0
wan
213.124.165.1
0
Web Interface
1.
Select the Routes item in the Status dropdown menu in the menu bar
2.
Check the Show all routes checkbox and click the Apply button
3.
The main window will list the active routing table, including the core routes
Tip: Understanding output from the routes command
For detailed information about the output of the CLI routes command. Please see the
CLI Reference Guide.
4.2.3. Route Failover
Overview
NetDefend Firewalls are often deployed in mission-critical locations where availability and
connectivity is crucial. For example, an enterprise relying heavily on access to the Internet could
have operations severely disrupted if a single connection to the external Internet via a single Internet
Service Provider (ISP) fails.
It is therefore not unusual to have backup Internet connectivity using a secondary ISP. The
connections to the two service providers often use different routes to avoid a single point of failure.
To allow for a situation with multiple ISPs, NetDefendOS provides a Route Failover capability so
that should one route fail, traffic can automatically failover to another, alternate route. NetDefendOS
implements route failover through the use of Route Monitoring in which NetDefendOS monitors the
availability of routes and then switches traffic to an alternate route should the primary, preferred
route fail.
4.2.3. Route Failover
Chapter 4. Routing
156
Summary of Contents for DFL-1600 - Security Appliance
Page 27: ...1 3 NetDefendOS State Engine Packet Flow Chapter 1 NetDefendOS Overview 27 ...
Page 79: ...2 7 3 Restore to Factory Defaults Chapter 2 Management and Maintenance 79 ...
Page 146: ...3 9 DNS Chapter 3 Fundamentals 146 ...
Page 227: ...4 7 5 Advanced Settings for Transparent Mode Chapter 4 Routing 227 ...
Page 241: ...5 4 IP Pools Chapter 5 DHCP Services 241 ...
Page 339: ...6 7 Blacklisting Hosts and Networks Chapter 6 Security Mechanisms 339 ...
Page 360: ...7 4 7 SAT and FwdFast Rules Chapter 7 Address Translation 360 ...
Page 382: ...8 3 Customizing HTML Pages Chapter 8 User Authentication 382 ...
Page 386: ... The TLS ALG 9 1 5 The TLS Alternative for VPN Chapter 9 VPN 386 ...
Page 439: ...Figure 9 3 PPTP Client Usage 9 5 4 PPTP L2TP Clients Chapter 9 VPN 439 ...
Page 450: ...9 7 6 Specific Symptoms Chapter 9 VPN 450 ...
Page 488: ...10 4 6 Setting Up SLB_SAT Rules Chapter 10 Traffic Management 488 ...
Page 503: ...11 6 HA Advanced Settings Chapter 11 High Availability 503 ...
Page 510: ...12 3 5 Limitations Chapter 12 ZoneDefense 510 ...
Page 533: ...13 9 Miscellaneous Settings Chapter 13 Advanced Settings 533 ...










































