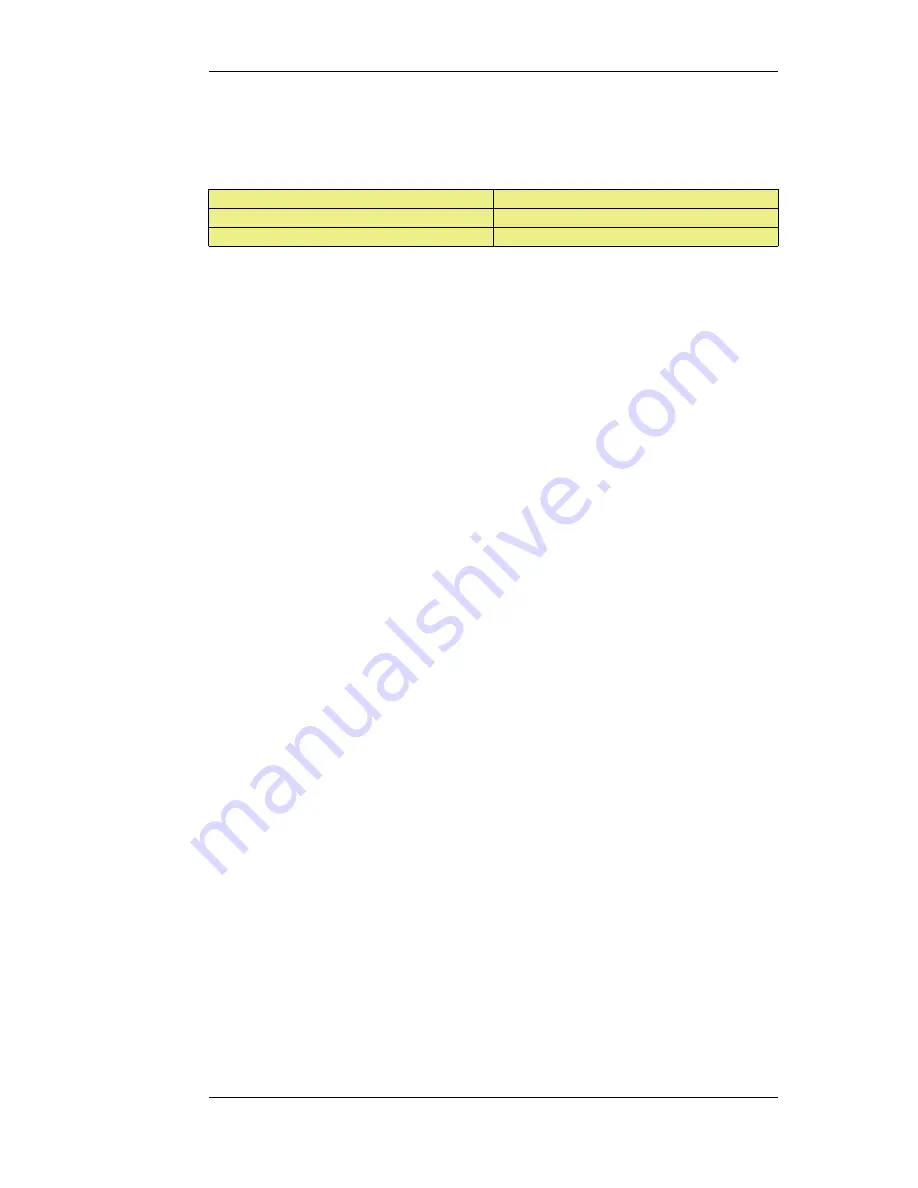
mode. Two VLAN interfaces with the same VLAN ID are defined on the two physical interfaces
and they are called vlan5_if1 and vlan5_if2.
For the VLAN to operate in transparent mode we create a routing table with the ordering set to only
and which contains the following 2 switch routes:
Network
Interface
all-nets
vlan5_if1
all-nets
vlan5_if2
Instead of creating individual entries, an interface group could be used in the above routing table.
No other non-switched routes should be in this routing table because traffic that follows such routes
will be tagged incorrectly with the VLAN ID.
Finally, we must associate this routing table with its VLAN interface by defining a Policy Based
Routing Rule.
Enabling Transparent Mode Directly on Interfaces
The recommended way to enable Transparent Mode is to add switch routes, as described above. An
alternative method is to enable transparent mode directly on an interface (a check box for this is
provided in the graphical user interfaces). When enabled in this way, default switch routes are
automatically added to the routing table for the interface and any corresponding non-switch routes
are automatically removed. This method is used in the detailed examples given later.
High Availability and Transparent Mode
Switch Routes cannot be used with High Availability and therefore true transparent mode cannot be
implemented with a NetDefendOS High Availability Cluster.
Instead of Switch Routes the solution in a High Availability setup is to use Proxy ARP to separate
two networks. This is described further in Section 4.2.6, “Proxy ARP”. The key disadvantage with
this approach is that firstly, clients will not be able to roam between NetDefendOS interfaces,
retaining the same IP address. Secondly, and more importantly, their network routes will need to be
manually configured for proxy ARP.
Transparent Mode with DHCP
In most Transparent Mode scenarios, the IP address of users is predefined and fixed and is not
dynamically fetched using DHCP. Indeed, the key advantage of Transparent Mode is that these
users can plug in anywhere and NetDefendOS can route their traffic correctly after determining their
whereabouts and IP address through ARP exchanges.
However, a DHCP server could be used to allocate user IP addresses in a Transparent Mode setup if
desired. With Internet connections, it may be the ISP's own DHCP server which will hand out public
IP addresses to users. In this case, NetDefendOS MUST be correctly configured as a DHCP Relayer
to forward DHCP traffic between users and the DHCP server.
It may be the case that the exact IP address of the DHCP server is unknown but what is known is the
Ethernet interface to which the DHCP server is connected. To enable DHCP requests to be relayed
through the firewall, the following steps are needed:
•
Define a static route which routes the IP address 255.255.255.255 to the interface on which the
DHCP server is found.
•
Define a static ARP table entry which maps the MAC address FF-FF-FF-FF-FF-FF to the IP
address 255.255.255.255.
4.7.1. Overview
Chapter 4. Routing
216
Summary of Contents for DFL-1600 - Security Appliance
Page 27: ...1 3 NetDefendOS State Engine Packet Flow Chapter 1 NetDefendOS Overview 27 ...
Page 79: ...2 7 3 Restore to Factory Defaults Chapter 2 Management and Maintenance 79 ...
Page 146: ...3 9 DNS Chapter 3 Fundamentals 146 ...
Page 227: ...4 7 5 Advanced Settings for Transparent Mode Chapter 4 Routing 227 ...
Page 241: ...5 4 IP Pools Chapter 5 DHCP Services 241 ...
Page 339: ...6 7 Blacklisting Hosts and Networks Chapter 6 Security Mechanisms 339 ...
Page 360: ...7 4 7 SAT and FwdFast Rules Chapter 7 Address Translation 360 ...
Page 382: ...8 3 Customizing HTML Pages Chapter 8 User Authentication 382 ...
Page 386: ... The TLS ALG 9 1 5 The TLS Alternative for VPN Chapter 9 VPN 386 ...
Page 439: ...Figure 9 3 PPTP Client Usage 9 5 4 PPTP L2TP Clients Chapter 9 VPN 439 ...
Page 450: ...9 7 6 Specific Symptoms Chapter 9 VPN 450 ...
Page 488: ...10 4 6 Setting Up SLB_SAT Rules Chapter 10 Traffic Management 488 ...
Page 503: ...11 6 HA Advanced Settings Chapter 11 High Availability 503 ...
Page 510: ...12 3 5 Limitations Chapter 12 ZoneDefense 510 ...
Page 533: ...13 9 Miscellaneous Settings Chapter 13 Advanced Settings 533 ...
















































