•
Dropping email which has a very high probability of being spam.
•
Letting through but flagging email that has a moderate probability of being spam.
The NetDefendOS Anti-Spam Implementation
SMTP functions as a protocol for sending emails between servers. NetDefendOS applies Spam
filtering to emails as they pass through the NetDefend Firewall from an external remote SMTP
server to a local SMTP server (from which local clients will later download their emails). Typically,
the local, protected SMTP server will be set up on a DMZ network and there will usually be only
one "hop" between the sending server and the local, receiving server.
DNSBL Databases
A number of trusted organizations maintain publicly available databases of the origin IP address of
known spamming SMTP servers and these can be queried over the public Internet. These lists are
known as DNS Black List (DNSBL) databases and the information is accessible using a standardized
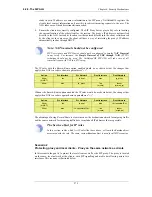
query method supported by NetDefendOS. The image below illustrates all the components involved:
DNSBL Server Queries
When the NetDefendOS Anto-Spam filtering function is configured, the IP address of the email's
sending server is sent to one or more DNSBL servers to find out if any DNSBL servers think the
email is from a spammer or not. NetDefendOS examines the IP packet headers to do this.
The reply sent back by a server is either a not listed response or a listed response. In the latter case
of being listed, the DSNBL server is indicating the email might be spam and it will usually also
provide information known as a TXT record which is a textual explanation for the listing.
Figure 6.5. Anti-Spam Filtering
Creating a DNSBL Consesus
The administrator can configure the NetDefendOS SMTP ALG to consult multiple DNSBL servers
in order to form a consensus opinion on an email's origin address. For each new email, configured
6.2.5. The SMTP ALG
Chapter 6. Security Mechanisms
263
Summary of Contents for DFL-1600 - Security Appliance
Page 27: ...1 3 NetDefendOS State Engine Packet Flow Chapter 1 NetDefendOS Overview 27 ...
Page 79: ...2 7 3 Restore to Factory Defaults Chapter 2 Management and Maintenance 79 ...
Page 146: ...3 9 DNS Chapter 3 Fundamentals 146 ...
Page 227: ...4 7 5 Advanced Settings for Transparent Mode Chapter 4 Routing 227 ...
Page 241: ...5 4 IP Pools Chapter 5 DHCP Services 241 ...
Page 339: ...6 7 Blacklisting Hosts and Networks Chapter 6 Security Mechanisms 339 ...
Page 360: ...7 4 7 SAT and FwdFast Rules Chapter 7 Address Translation 360 ...
Page 382: ...8 3 Customizing HTML Pages Chapter 8 User Authentication 382 ...
Page 386: ... The TLS ALG 9 1 5 The TLS Alternative for VPN Chapter 9 VPN 386 ...
Page 439: ...Figure 9 3 PPTP Client Usage 9 5 4 PPTP L2TP Clients Chapter 9 VPN 439 ...
Page 450: ...9 7 6 Specific Symptoms Chapter 9 VPN 450 ...
Page 488: ...10 4 6 Setting Up SLB_SAT Rules Chapter 10 Traffic Management 488 ...
Page 503: ...11 6 HA Advanced Settings Chapter 11 High Availability 503 ...
Page 510: ...12 3 5 Limitations Chapter 12 ZoneDefense 510 ...
Page 533: ...13 9 Miscellaneous Settings Chapter 13 Advanced Settings 533 ...