sends its own IP address as contact information to the SIP proxy. NetDefendOS registers the
client's local contact information and uses this to redirect incoming requests to the user. The
ALG takes care of the address translations needed.
4.
Ensure the clients are correctly configured. The SIP Proxy Server plays a key role in locating
the current location of the other client for the session. The proxy's IP address is not specified
directly in the ALG. Instead its location is either entered directly into the client software used
by the client or in some cases the client will have a way of retrieving the proxy's IP address
automatically such as through DHCP.
Note: NAT traversal should not be configured
SIP User Agents and SIP Proxies should not be configured to employ NAT Traversal
in any setup. For instance, the Simple Traversal of UDP through NATs (STUN)
technique should not be used. The NetDefendOS SIP ALG will take care of all
traversal issues with NAT in a SIP setup.
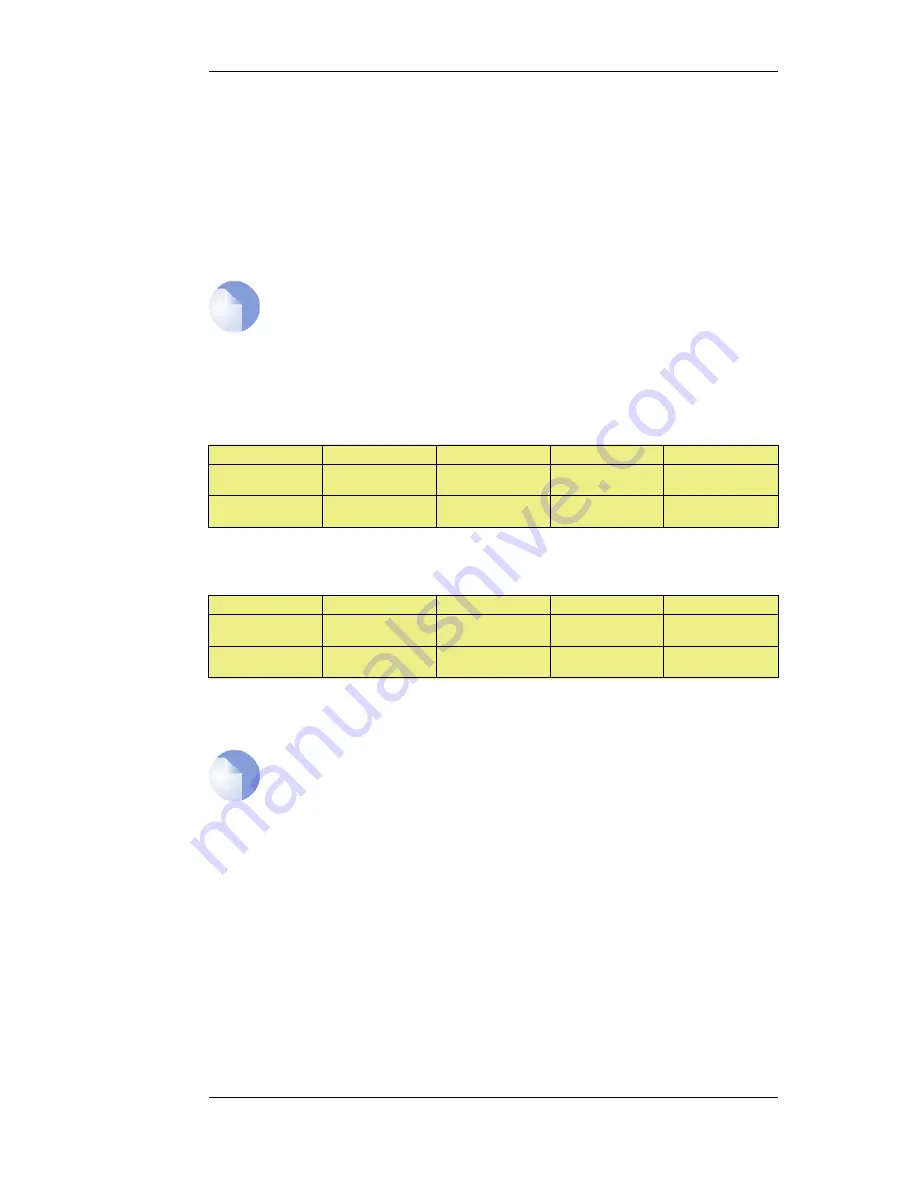
The IP rules with the Record-Route option enabled would be as shown below, the changes that
apply when NAT is used are shown in parentheses "(..)".
Action
Src Interface
Src Network
Dest Interface
Dest Network
Allow
(or NAT)
lan
lannet
wan
ip_proxy
Allow
wan
ip_proxy
lan
(or core)
lannet
(or wan_ip)
Without the Record-Route option enabled the IP rules would be as shown below, the changes that
apply when NAT is used are again shown in parentheses "(..)".
Action
Src Interface
Src Network
Dest Interface
Dest Network
Allow
(or NAT)
lan
lannet
wan
<All possible IPs>
Allow
wan
<All possible IPs>
lan
(or core)
lannet
(or ipwan)
The advantage of using Record-Route is clear since now the destination network for outgoing traffic
and the source network for incoming traffic have to include all IP addresses that are possible.
The Service object for IP rules
In this section, tables which list IP rules like those above, will omit the Service object
associated with the rule. The same, custom Service object is used for all SIP scenarios.
Scenario 2
Protecting proxy and local clients - Proxy on the same network as clients
In this scenario the goal is to protect the local clients as well as the SIP proxy. The proxy is located
on the same, local network as the clients, with SIP signalling and media data flowing across two
interfaces. This scenario is illustrated below.
6.2.8. The SIP ALG
Chapter 6. Security Mechanisms
275
Summary of Contents for DFL-1600 - Security Appliance
Page 27: ...1 3 NetDefendOS State Engine Packet Flow Chapter 1 NetDefendOS Overview 27 ...
Page 79: ...2 7 3 Restore to Factory Defaults Chapter 2 Management and Maintenance 79 ...
Page 146: ...3 9 DNS Chapter 3 Fundamentals 146 ...
Page 227: ...4 7 5 Advanced Settings for Transparent Mode Chapter 4 Routing 227 ...
Page 241: ...5 4 IP Pools Chapter 5 DHCP Services 241 ...
Page 339: ...6 7 Blacklisting Hosts and Networks Chapter 6 Security Mechanisms 339 ...
Page 360: ...7 4 7 SAT and FwdFast Rules Chapter 7 Address Translation 360 ...
Page 382: ...8 3 Customizing HTML Pages Chapter 8 User Authentication 382 ...
Page 386: ... The TLS ALG 9 1 5 The TLS Alternative for VPN Chapter 9 VPN 386 ...
Page 439: ...Figure 9 3 PPTP Client Usage 9 5 4 PPTP L2TP Clients Chapter 9 VPN 439 ...
Page 450: ...9 7 6 Specific Symptoms Chapter 9 VPN 450 ...
Page 488: ...10 4 6 Setting Up SLB_SAT Rules Chapter 10 Traffic Management 488 ...
Page 503: ...11 6 HA Advanced Settings Chapter 11 High Availability 503 ...
Page 510: ...12 3 5 Limitations Chapter 12 ZoneDefense 510 ...
Page 533: ...13 9 Miscellaneous Settings Chapter 13 Advanced Settings 533 ...